Yo hello everyone! Hope everyone is doing well and fine. I’ve only just recently finished my exam and the semester. It’s kind of late for a write-up on GCC, but still I am gonna do it! Sorry if some of guys were not mentioned in this, but trust me I really love y’all and honestly I miss the moments we made throughout the camp 🥹
Let’s start!
Context
For this year Global Cybersecurity Camp (GCC), I was one of the 5 selected student to represent Malaysia in a week-long program where students from different countries come together to learn about cybersecurity. We'll be building friendships and learning together! You can find more info here: https://gcc.ac
This year’s GCC is in Chonburi, Thailand! 🇹🇭
Departing from the KLIA airport
I arrived at Kuala Lumpur International Airport (KLIA) early in the morning around 8:00 A.M. We Malaysian students, gathered together at a restaurant while waiting for the check-in time.


Arrival at the GCC Venue! - Day 0
I skipped a lot of stuff here, but we arrived at the GCC venue at around 4:00 P.M. (Thailand time).
While at the receptionist, I saw a bunch of students from different countries and I was feeling so excited to get to know them all, but was still shy at the time.
And coincidentally, I saw a familiar face from Hack in The Box (HITB) Phuket last year, which is River! I remember him as one of the tallest guys in the HITB Crew and also a fellow web player 😶🌫️
On this day too, each of the country participants must introduce themself to other countries. During the introduction for each country, I was so amazed by how great the other participants are. All of them had really amazing skills, achievements and findings which makes me feel kind of small but also fired up!
I’ve also met my roommate Anikait! A really cool guy hardware hacking guy from team bi0s. We’ve also spent some time talking about our interest in cybersecurity before the introduction session.




Meeting my groupmates!
Each of the GCC participants were assigned into a group. The best part is, each and every member of the group is from a different country!
My group is actually filled with really really cool and great people.
In our group we have:
- Pong (Actually a developer from Thailand! I can tell based on how he did his commit message and he himself said so)
- Robbert (Truly pro pwn player from Vietnam and also a fan of Mikasa Mikoto <3)
- Keisuke (A really Kakkoii) risk management guy from Japan, it’s always nice to talk about him about nihon-specific things and also test and improve my Japanese speaking skills xD)
- Slash (A really cool fellow web player from Taiwan, fr he’s really cool and always love to visit Malaysia as his choice of place for tourism)
As a group work, we were given a task to create a Maltego plugin to parse mobile phone dumps data. We’ve made it open source and modular for each and every functions. I’ll leave the Github project link at the end of this blog post.

Training Sessions
Deep Dive into Active Directory(AD) Attack Techniques
For this session, we were taught by Mr Mars Cheng from Taiwan about attacking Active Directory (AD) on Windows. It’s been a while since I’ve last worked with AD deployment since my WorldSkills ITNSA competing days, and it’s such a refreshment. All this while, I’ve never know how to hack an AD, and this session has taught me a lot about AD hacking.
How (not) to build a vulnerable LLM web app
This is the session I was looking forward the most, even before GCC because of the term “web” and “LLM” in one title. This session were taught by Mr Shota Shinogi from Japan. We learned a lot about prompt injection and how LLM web apps can be exploited in a scary way (if without enough sanitization, checks etc).
I’ve also had the chance to talk with Mr Shota Shinogi at the end of the session, and captured few insights from him about how LLM can be used to also check for LLM prompt injection.
Check out
Handling Threat Intelligence: Techniques of consuming and creating threat intelligence
This session were taught by Mr Tomohisa Ishikawa from Japan. In this session we were taught about how threat intelligence works and how certain threats could be identified early on. We also had a session of working through the logs, finding suspicious activities in the event logs and identifying attacks.
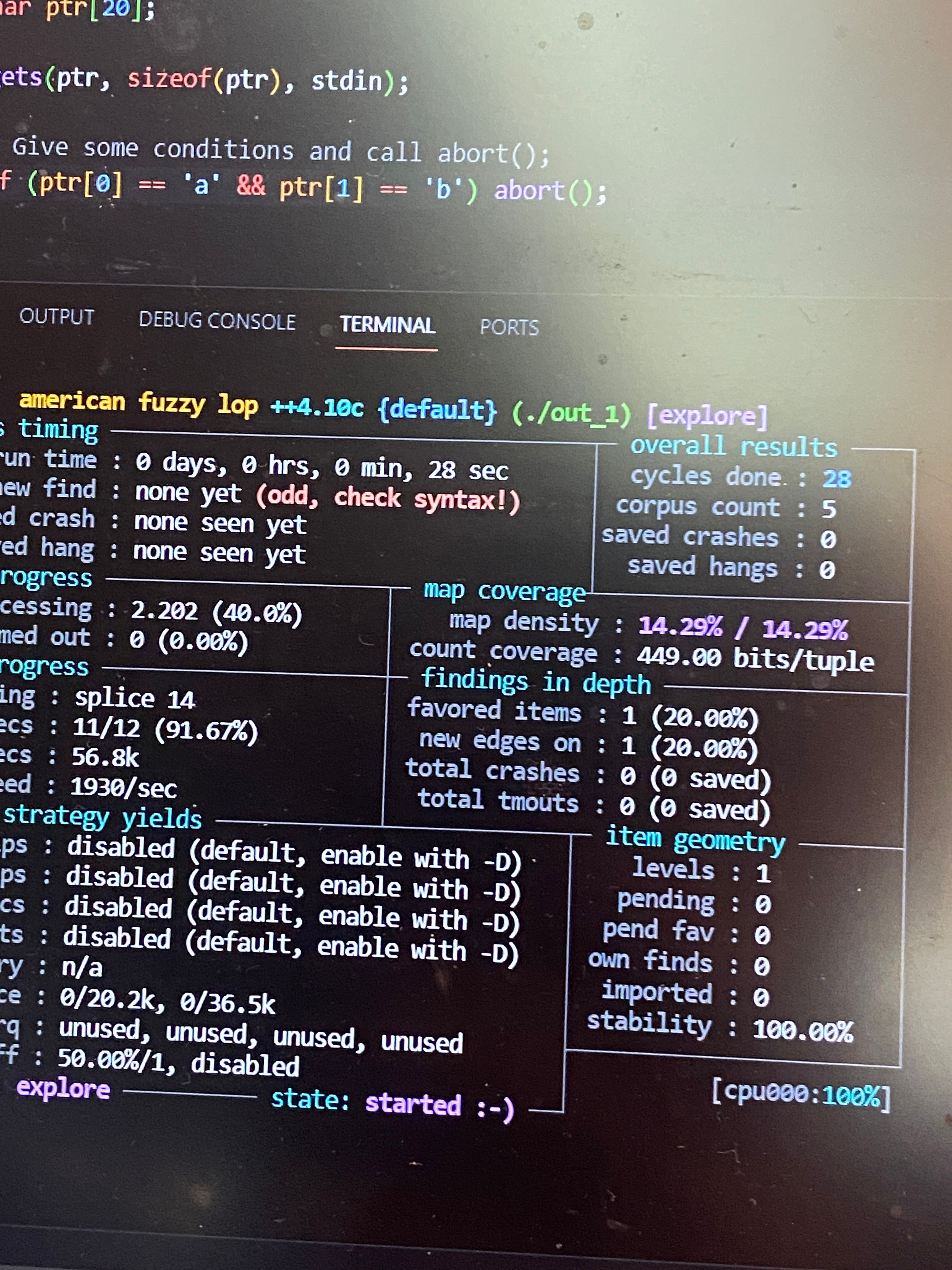
Fuzzing in the kernel world
In this session, we were taught about fuzzing a binary input. The session were taught by Ms Yi-Han Wang from Taiwan. Honestly, it’s my first time fuzzing a binary using AFL++ and it was actually very fun! We were fuzzing a lot of inputs for the applications, and it felt so satisfying when we found a crash. Though, when we are nearing end part of the session, I couldn’t wrap my head around virtualization stuff that were being taught. 😵💫 But still, fuzzing is fun!
Hunting with a dinosaur
Another one of my most anticipated session in GCC, hunting with the Velociprator tool. I first heard about the tool from a friend of mine in Malaysia (sensei nxur0se) and he said it is a very useful tool in threat hunting but I’ve never had the chance to test it. The session were taught by Mr Andreas van Leeuwen Flamino from Arab Emirates. In this session, we used Velociraptor to collect various kind of artifacts and I could tell you, it is such a very powerful tool! It has live analysis, user-friendly interface, Hayabusa built-in and more! Definitely one of the tools I would love to use in the future.
Hands-on Car Hacking
This is the longest session among all GCC training sessions and actually one of the session I had the most fun with! This session were taught by Mr Kamel Ghali from Japan. In this session, were taught about how a car could be hacked and controlled through a CAN bus system. We were also given a chance to play with real hardware in a car and it was so amazing to see everyone working on exploiting/controlling the hardware by sending signals to CAN bus.
10/10 would love to hack my own car at home.
Practical Malware Analysis and .NET Reversing Based on Real-World Cases
This session is about reversing .NET Malware specifically Redline . The session were taught by Mr Wei-Chieh Chao and Mr Yi-Hsien Chen from Taiwan. We learned how to use DnSPY and how we could reverse .NET binaries and turn off certain checks when reversing malware. It was a very fun session as someone who had never reversed a .NET binary before this!
End (actually there’s a lot more but I’ll end it here)
The Global Cybersecurity Camp (GCC) 2023 in Chonburi, Thailand was an unforgettable experience filled with learning, collaboration, and making new friendships from around the world. Being selected as one of the representatives from Malaysia was a privilege, and the week-long program was packed with insightful sessions, hands-on workshops, and memorable moments.
We were privileged to learn from experts like Mr Mars Cheng, Mr Shota Shinogi, Mr Tomohisa Ishikawa, Ms Yi-Han Wang, and Mr Kamel Ghali, among others. Their expertise, coupled with hands-on activities, allowed us to expand our skills and understanding of the cybersecurity landscape.
One of the most rewarding aspects of GCC was working with my groupmates on a Maltego plugin project. Collaborating with individuals from Thailand, Vietnam, Japan, and Taiwan brought diverse perspectives to the table. Together, we created an open-source and modular solution for parsing mobile phone dump data, fostering teamwork and innovation.
I would like to say thanks to the GCC committee for the welcoming stay and also all the sponsors. Also thanks to Sherpasec for selecting me and sponsoring me to represent Malaysia as part of this year’s GCC.
And also I miss y’all from GCC!!!!!!!!!!!! Hopefully we can meet again some other time 🥹 🥹 🥹 🥹
Here’s the maltego modular scripts we made:
https://github.com/vicevirus/maltego-auto-android-data-dump
Okay, now time for image dump!

















 vicevirus’ Blog
vicevirus’ Blog